This content is viewable by Everyone
SEP for Linux: Install Guide
- Owner Team: IT Security
-
Service:Symantec Endpoint Protection (SEP)
System requirements
Broadcom maintains this webpage to list supported Linux distributions and kernels for each of the Symantec Endpoint Protection versions.
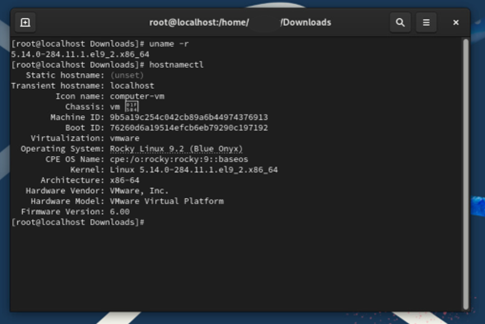
You can validate your Linux Distribution and Kernel Version in an elevated terminal command:
uname -r
Note: Some potential boot-time vulnerabilities may be present when using an older or unsupported kernel. To increase the security of this process, consider password protecting the GRUB bootloader.
Download the UCSF SEP client installer
- Verify you are on a UCSF connection (ethernet, UCSFwpa or vpn@UCSF).
- Go to https://software.ucsf.edu/content/endpoint-protection.
- Under Linux Downloads, click on the appropriate link
Uninstall old and other client security applications
- Note: You will need to uninstall any other anti-virus or endpoint protection programs you may have.
- As of this writing (6/27/2023), Symantec Endpoint Protection for Linux does not include Firewall and Intrusion Protection (IPS) components. Broadcom maintains a list of supported components for the Symantec Endpoint Protection application in their Frequently Asked Questions article for Linux Agents
Run the UCSF SEP client installer
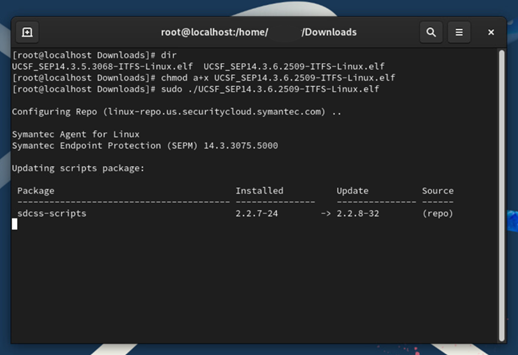
- Open terminal and navigate to the .elf file acquired from UCSF
- Grant the file execute permissions for your user or all users
chmod u+x YourFile.elfor
chmod a+x YourFile.elf
- Execute the installation file as a super user
sudo ./YourFile.elf
- Once the installation completes successfully, the installer will confirm the installed Daemons are running and the Modules are loaded.
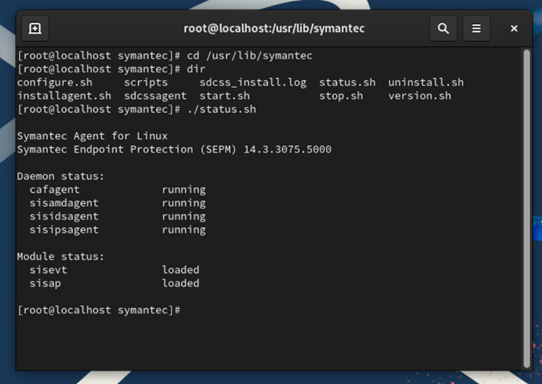
Verify Symantec Agent Status
You can validate the agent Daemon and Module status by executing
/usr/lib/symantec/status.sh
Additional scrips are present in this directory to start and stop the agent, and validate the installed product versions.
Note:
- The "sisevt" module is symevent, a kernel event monitor
- The "sisap" module is autoprotect, a real-time file scanner
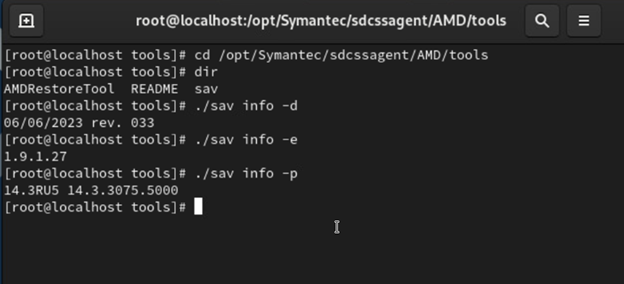
Managing your Linux client using the command line tool (sav)
Broadcom maintains documentation here on how to use the command line tool (sav) to manage the Auto-Protect settings, check the product and definition versions, configure manual and scheduled scan settings, and work with quarantined files. Note: this tool requires root privileges to run.
By default, this tool is installed to /opt/Symantec/sdcssagent/AMD/tools
SEP for Linux with Secure Boot enabled
Secure Boot is generally recommended as an additional measure of protection for systems, preventing malicious code from being inserted into the kernel. Secure Boot is the protocol that enables a safe and trusted path during the Linux boot process, using digital key pairs to check that SystemTap and other startup code hasn't been altered by a rootkit or similar mechanism.
When Secure Boot is enabled on a Linux system where SEP for Linux is deployed, some of SEP's functions may fail to start. Follow the procedure outlined in this Broadcom article to import the public key signing certificate (added to your agent when SEP is installed) with the MOK (Machine Owner Key) Manager.