Log in to see all content. Some content is hidden to the public.
Can't find what you're looking for? Help us improve the search functionality by reporting the expected results.
505 Results
IT Business Process Transformation
The Business Process Transformation team is all about making things work better. We redesign the way we do things to be more efficient, effective, and agile, all while ensuring satisfaction. We're driven by the need to grow and adapt to new challenges, always working towards our departmental goals.
IT Administration
Administrative Services is a UCSF IT combined team providing high-touch, cross-functional human resource management and development support for IT leaders and staff across the organization.
Enterprise Portfolio Management
The Enterprise Portfolio Management (EPM) domain serves as a centralized authority responsible for assisting in evaluating, prioritizing, and selecting projects and initiatives that align with the organization's strategic objectives. It establishes a framework for evaluating project proposals, assessing their potential risks and benefits, and determining their feasibility and alignment with the organization's mission, vision, and values.
IT Finance
The IT Finance and Campus Finance teams are responsible for the stewardship of IT’s financial resources (~$300M in annual spend and ~900 FTE). We ensure both IT’s and the institution's fiscal goals are met in compliance with accounting, regulatory, and other policies.
IT Project Management Office (PMO)
The UCSF IT Project Management Office (PMO) provides project management services across a wide range of technologies and methodologies in support of all missions across the enterprise. We support collaboration and value delivery through the definition of standards supportive of delivering projects at scale. Reach out via the OCIO mailbox at [email protected].
Zoom Patches Critical Vulnerability in Windows Applications
Zoom has released a security bulletin to address a critical vulnerability in its Windows applications. The attack is described as an improper input validation that could allow an attacker with network access to escalate privileges.For a complete description of the vulnerabilities and affected systems go to Zoom Security Bulletin.IT SecurityRead more about IT Security service offerings.
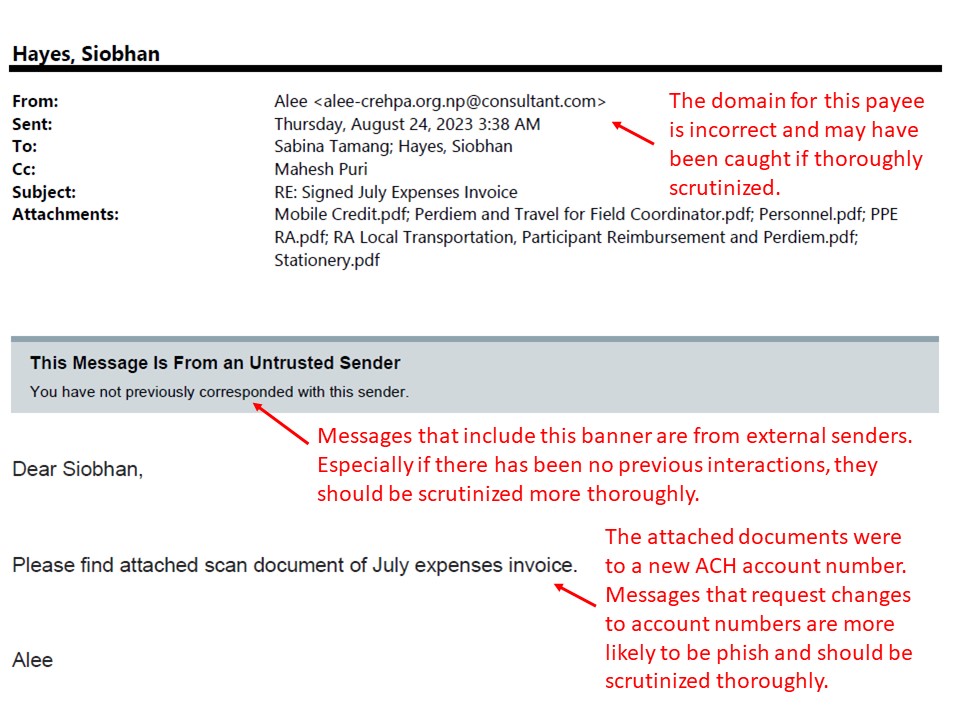
Jun - Nov 2023: Supply Chain Management / Accounts Payable ACH Fraud
Picture of One of the Phish
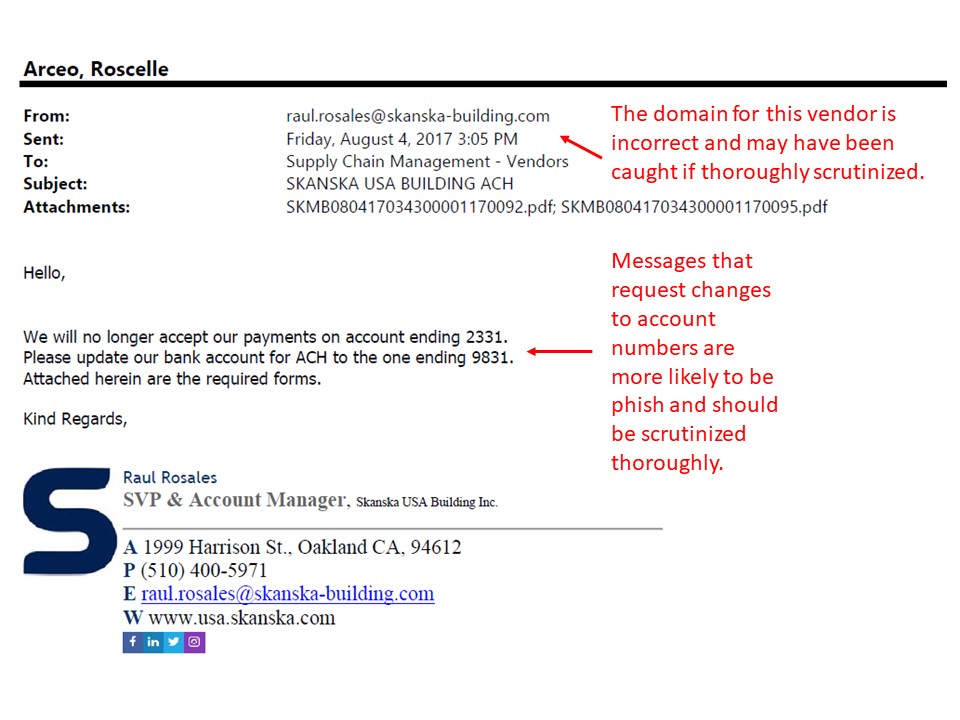
Aug 2017: Supply Chain Management / Vendor Relations ACH Fraud
Picture of Real Phish
Threat Alert: Fraudul
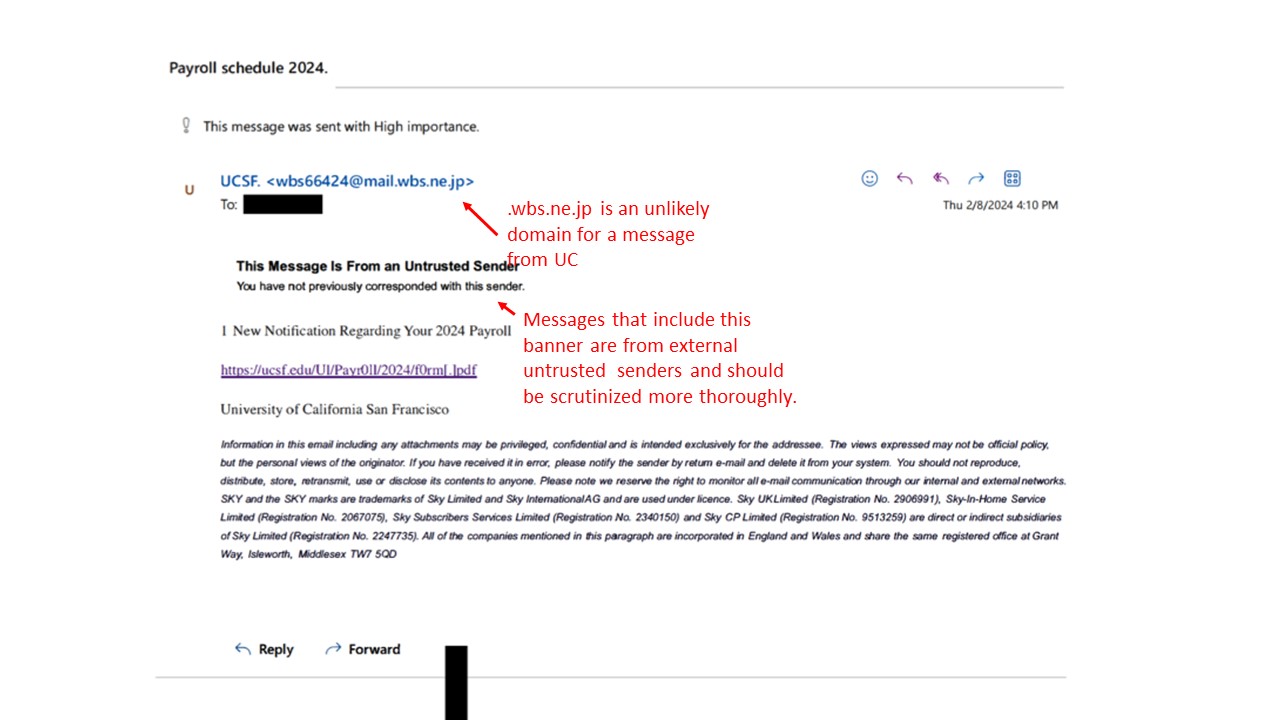
Feb: 2024: Real Phish Received at UCSF - Payroll Lure Harvesting Credentials
Picture of Actual Phish:
Picture of Actual Landi
Feb 2024: Deepfake Scam Imitating CFO
Threat Alert: Deepfake Scam Targeting Financial Transactions An employee attended a video conference call with seemingly authentic colleagues, all of whom were later revealed to be deepfake representations. The worker, initially suspicious of a phishing email, was convinced by the realistic appearance and voices of the deepfake participants during the video call. Subsequently, the employee authorized a large financial transaction, thinking it was a legitimate request initiated by the CFO.