This content is viewable by Everyone
Apr 2024: Microsoft Lure - HTML Files Leading to Malware Installation
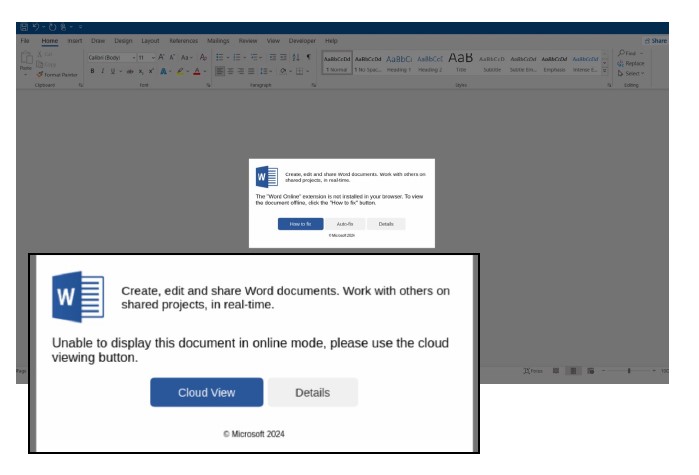
Threat Alert: Microsoft Lure - HTML Files Leading to Malware Installation
- Threat actors are using HTML attachments designed to appear like Microsoft Word documents to deliver malware.
- In this attack, threat actors send messages with lures designed to encourage end users to download and open an HTML attachment.
- When double-clicked, the HTML attachment will open in the user’s default browser rendering a spoofed or fake page that is web-enabled like normal websites.
- In these web pages, popups appear that encourage the user to click to “fix” the document. Clicking will then initiate a download resulting in loader malware deployment.
Key Action: Report Suspicious Emails
- Never interact with an unexpected HTML attachment, even if it appears to come from a familiar source. Verify the legitimacy of ANY unsolicited file before you preview, open, or download it.
- Question uncommon sender urgency. Be wary of urgent requests from unfamiliar senders. Verify legitimacy through official channels before acting on unsolicited requests.
- Report ANY suspicious emails using the Phish Alarm button.