This content is viewable by Everyone
Apr 2025: AnyDesk Control
Threat Alert: AnyDesk Control
- AnyDesk and similar remote monitoring and management (RMM) tools let IT professionals monitor endpoints remotely, but threat actors can exploit their capabilities and trusted status.
- The attack uses social engineering techniques to manipulate recipients into taking actions that give the attacker access to their devices.
- Threat actors frequently try to deliver malicious RMM payloads to end users. The social engineering tactics used to access RMM sessions on victim machines in this campaign represent a new threat.
How is it used in the wild?
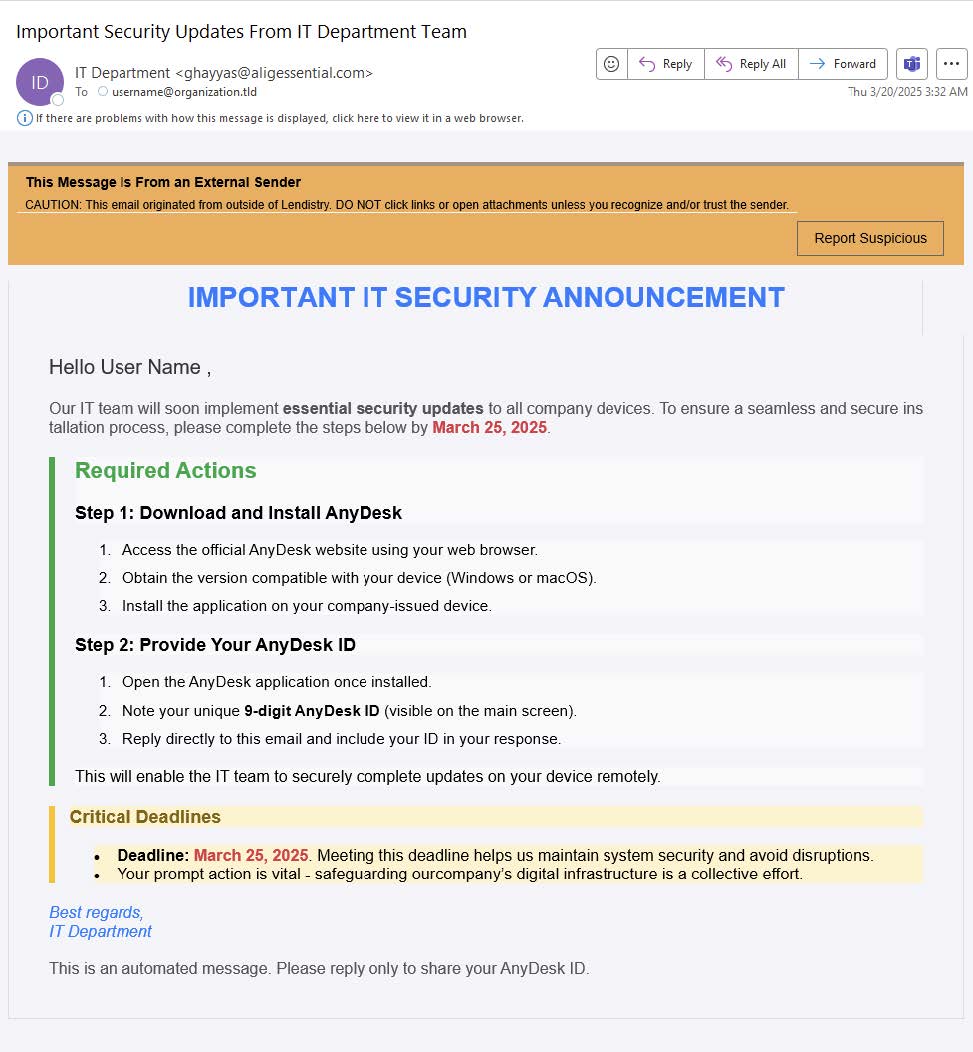
- Threat actors send emails that appear to come from the recipient’s organization, identifying the sender as “IT Department”, ”IT Security Team”, and “Security Updates.
- The email pressures recipients to install or update AnyDesk by imposing a false deadline, warning that non-compliance may result in increased security risks.
- Recipients are prompted to follow step-by-step instructions to recipients to download and install legitimate instances of AnyDesk.Following installation, users are directed to provide their unique AnyDesk identifier to an actor-controlled mailbox.
- If successfully acquired, the unique AnyDesk identifier allows threat actors to access victim endpoints.
Key Action: Stay Alert!
- Remain alert to phishing indicators, such as mismatches in email signatures, sender information, subject, and attachments.
- Stay alert for email messages requesting security-related tasks or the installation of software or applications.
- Exercise the same caution for unique IDs (like AnyDesk or other software) as you would a password or passcode or other credentials. Keep these unique identifiers private.
- Report ANY suspicious emails via Phish Alarm.