This content is viewable by Everyone
Apr 2025: PROOFPOINT IMPERSONATION
Threat Alert: PROOFPOINT IMPERSONATION
- The threat is a Phishing-as-a-Service (PhaaS) platform that specializes in stealing Microsoft 365 login credentials, user cookies, Microsoft 365 data, and system information.
- Information collected enables attackers to bypass MFA protections, which can lead to account compromise, even on many systems protected by multifactor authentication.
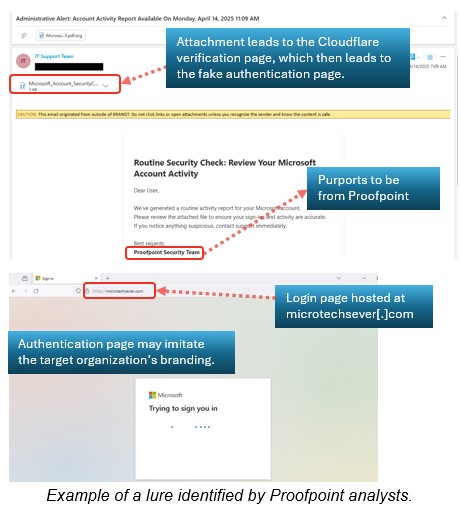
- The threat can also mimic a company’s branding to create a more convincing authentication page.
How is it used in the wild?
- Threat actors used a PhaaS platform to impersonate Proofpoint, sending emails that looked like security account notifications.
- Example subject lines included:
- Compliance Reminder: Monthly Activity Verification On [date]
- Administrative Alert: Basic Routine Check Report Available on [date]
- Administrative Alert: Account Activity Report Available on [date]
- The messages had attachments that, when opened, led the user to a fake Microsoft 365 login page via a Cloudflare verification.
- The login page featured the organization’s branding while collecting the user’s credentials, 2FA token, and session cookie.
- The information gathered could lead to account compromise.
Key Action: Stay Alert!
- Cybercriminals regularly mimic legitimate services like Proofpoint. Cybercriminals impersonate legitimate services to gain credibility.
- Check emails carefully, paying attention to the URL, sender, subject, and attachments. Be wary of URLs that push you to external sites for "authentication.”
- Remain alert to phishing indicators. Mismatches between sending addresses and an organization’s name are always warning signs.
- Report ANY suspicious emails via Phish Alarm.