This content is viewable by Everyone
Aug 2025: QR CODE FIDO ATTACK
Threat Alert: QR CODE FIDO ATTACK
- Fast Identity Online (FIDO) keys are currently one of the most secure forms of multi-factor authentication (MFA) because they cannot be easily duplicated and use cryptography. The open standards under FIDO include hardware keys, one-time passwords, and push notification authentication
- Threat actors could use social engineering to authenticate via FIDO by luring users into scanning a QR code.
How is it used in the wild?
- Threat actors could use the cross-device login function of a FIDO app to gain unauthorized password access to multiple accounts.
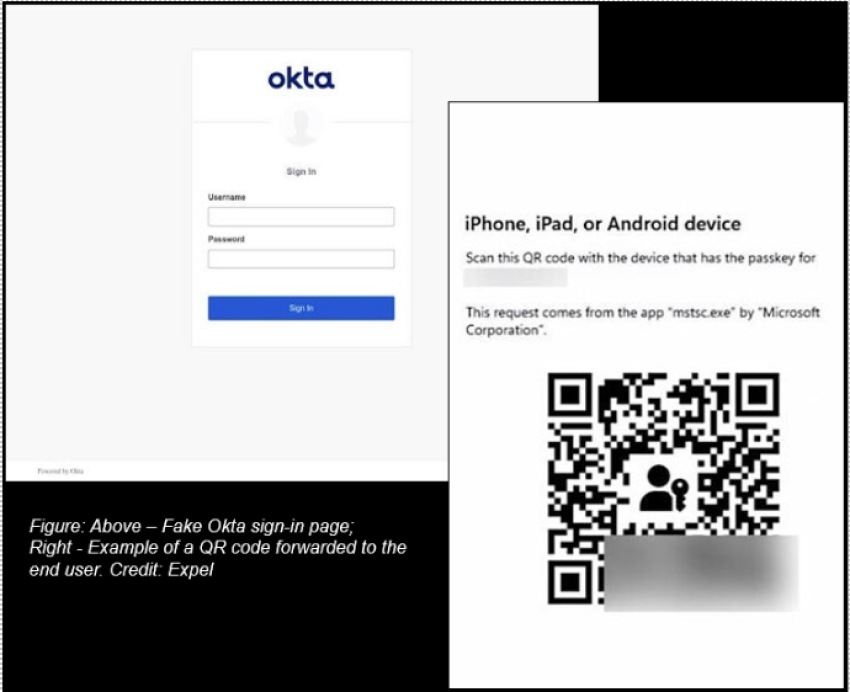
- The attack begins with a phishing email requesting that end users log in via Okta. The users would then be directed to a fake Okta authentication page with adversary-in-the-middle (AitM) capabilities.
- Users’ FIDO apps should have prevented the threat actor from logging into the account. However, the phishing page automatically sent the credentials to the legitimate Okta page and returned a QR code to the user. If scanned by the user without Client-to-Authenticator Protocol (CTAP) enabled, the threat actor could gain unauthorized access to the account.
- While the attack successfully obtained password authentication, the MFA portion of all observed attacks failed due to FIDO specification requiring local proximity.
Key Action: Stay Alert!
- Do not click on sign-on links in emails.
- Check the URLs of any authentication page presented.
- Be wary of QR codes.
- Report ANY suspicious emails via Phish Alarm.