This content is viewable by Everyone
Dec 2022: Phish Alarm-Themed Lures Used in Credential Phishing Attacks
Threat Alert: What to Watch For
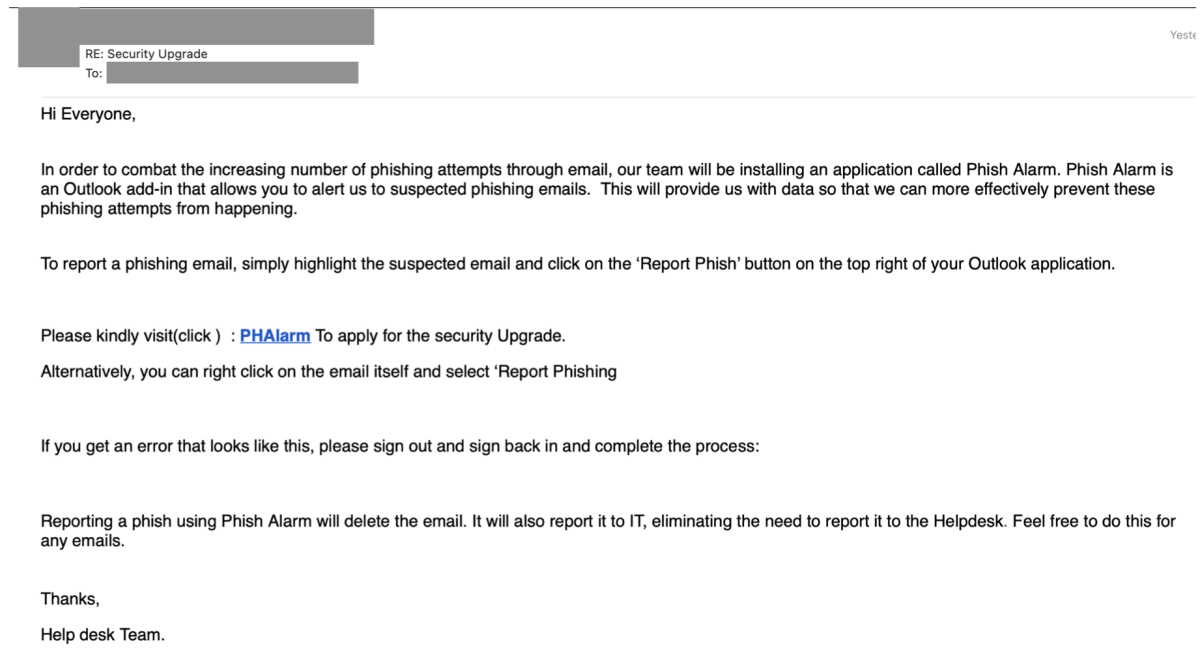
- Cybercriminals have launched phishing attacks claiming to originate from a company help desk team. The emails include links to a lookalike Outlook Web App page designed to steal user credentials.
- The emails encourage recipients to click the included link to install a Phish Alarm Outlook add-in.
- The emails attempt to exploit the security best practice of reporting suspicious emails to further increase the perceived legitimacy of the email.
- The emails contain slight spelling and grammar irregularities, such as capitalizing the “u” in “security Upgrade,” as well as not having a consistent spelling of the phrase “help desk.”
Key Action: Report Suspicious Emails
- Report ANY suspicious emails using the Phish Alarm button in your email menu bar.
- Remember: Our organization occasionally sends phishing simulations that are used to evaluate the potential impact of a real phishing attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Verify the legitimacy of any unsolicited/unexpected email before you interact with it, especially if it directs you to click on a link or asks you to provide credentials. It can be tempting to click on a “call-to-action,” especially regarding applying security upgrades. Remember, if you notice a subtle change or inconsistency within a message claiming to be from an internal department, don’t ignore it—report it.
- Follow company policy for upgrades and updates. Emails claiming to be from IT or help desk teams encouraging security downloads via a direct link can be especially tempting. However, always check for software updates directly at the source or by following organization-specified processes for confirming the availability of internal updates and where to find them.
- Be extremely cautious of emailed links that lead you to an account login page—even if the page looks “right.” It’s always safest to control your own path and log in via known, trusted channels.