This content is viewable by Everyone
Feb 2023: Valentine’s Day-Themed Lures
Threat Alert: What to Watch For
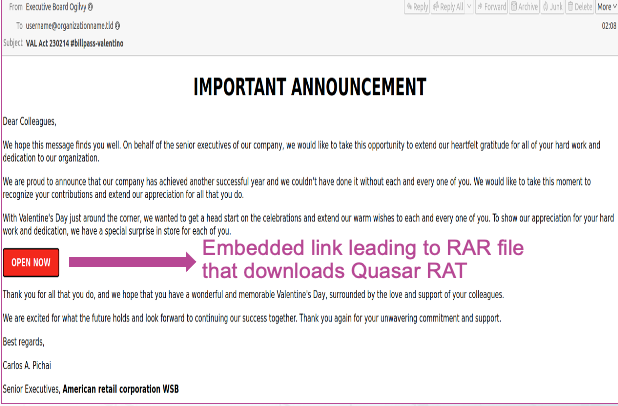
- Cybercriminals have launched phishing attacks claiming to be senior executives offering employees a Valentine’s Day-themed reward in appreciation of their work. The message purporting to be from executives might compel users to engage with the supposed employer-related communications.
- The promise of a reward or gift for the employee’s dedication to the organization entices recipients to click on a malicious link. Following the link leads to a malicious file download and subsequent installation of Quasar RAT.
- Cybersecurity researchers have seen attackers using phishing lures related to Valentine’s Day and are expected to continue throughout February. You could see these at work or in your personal accounts and on social media.
Key Action: Report Suspicious Emails
- Report ANY suspicious emails using the Phish Alarm button in your email menu bar.
- Remember: Our organization occasionally sends phishing simulations that are used to evaluate the potential impact of a real phishing attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Keep in mind that cybercriminals commonly leverage current events in phishing attacks. Attackers use holiday-themed lures, like Valentine’s Day, across various channels. That means you could see similar tactics being used on social media, lookalike websites, printed materials, and malicious and misleading ads.
- Be aware of enticing offers. Attackers try to manipulate people’s emotions in various ways, and rewards are common lures. The promise of a reward for hard work could trick many people.
- Never download attachments or “enable content” associated with unexpected messages. Never open, preview, or download an unexpected attachment, and never “enable content” or “enable macros” unless you are certain a file is safe. These actions can expose you to malware.
- Remain alert to phishing indicators. Mismatches between sending addresses and an organization’s name are always warning signs. Remember, if you notice a subtle change or inconsistency within a message claiming to be from an internal department, don’t ignore it—report it.