This content is viewable by Everyone
Jan 2023: Compensation-Themed Phishing Lures Harvest Microsoft Credentials
Threat Alert: What to Watch For
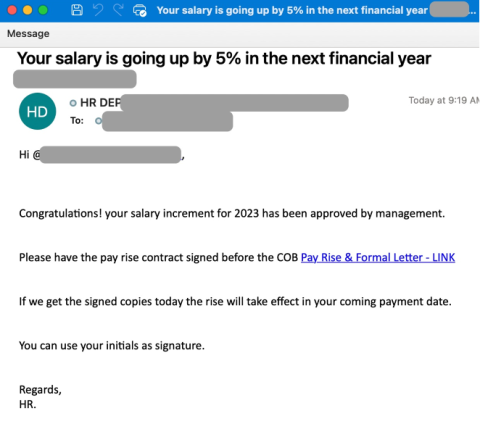
- Cybercriminals have launched a series of phishing attacks using timely email phishing lures related to annual compensation reviews and bonuses.
- The phishing emails encourage recipients to click a lure to confirm a payment-related change.
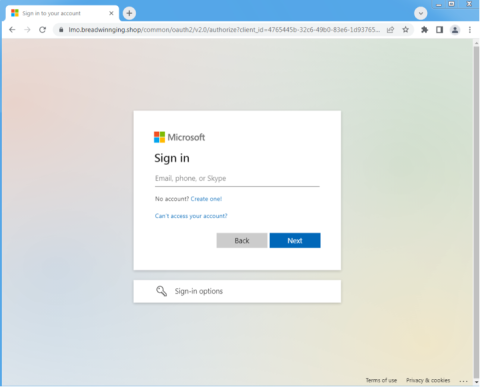
- Opening the link leads to a lookalike Microsoft login page, which is designed to steal credentials.
- The sending email address for the phishing emails is “hrdp” followed by a randomized string of letters and numbers.
- The email subject line is typically a variation of mentioning a raise and an apparent reference number, such as “Increased pay B2B1B207451” or “How much will your salary grow? B1B1B357950.”
Key Action: Report Suspicious Emails
- Report ANY suspicious emails using Phish Alarm button in your email menu bar.
- Remember: Our organization occasionally sends phishing simulations that are used to evaluate the potential impact of a real phishing attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Verify the legitimacy of any unsolicited/unexpected email before you interact with it, especially if it leads you to a login page asking for credentials. If you notice a subtle change or inconsistency within a message claiming to be from an internal department, don’t ignore it—report it.
- Be extremely cautious of emailed attachments that lead you to an account login page—even if the page looks “right.” It’s always safest to control your own path and log in via known, trusted channels.
- Familiarize yourself with standard payment processes. Communications regarding payments should only ever come from known, organizational email addresses. If in doubt, always navigate directly to internal portals to double check the legitimacy of payment-related changes or email the finance or HR teams before interacting with a message.
- Be cautious of unexpected emails related to timely events. Cybercriminals frequently tailor their phishing lures to actions related to specific times of year, such as annual compensation reviews, holiday bonuses, or tax season.