This content is viewable by Everyone
Jan 2023: Phishing Attacks Abuse Microsoft OneNote
Threat Alert: What to Watch For
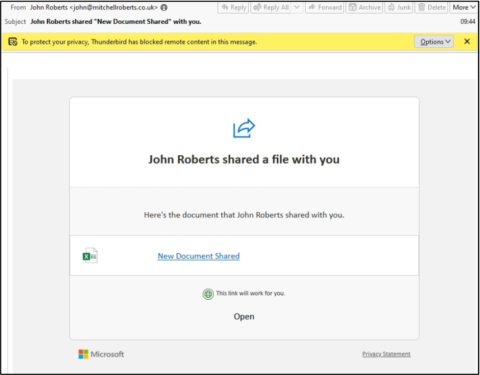
- Recent email-based attacks have abused Microsoft’s legitimate OneNote application to share malicious files. The emails use subject lines like “New Document Shared with you” and encourage the recipient to follow a link to view a shared OneNote file.
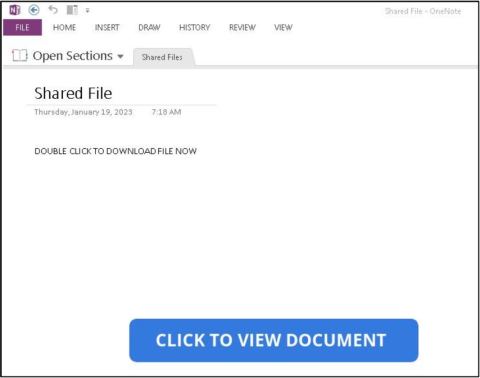
- The OneNote link leads recipients to a shared document which contains the text “DOUBLE CLICK TO DOWNLOAD THE FILE NOW.”
- Some attacks may also distribute similar malicious OneNote files as email attachments.
- Double clicking to install the file may prompt the recipient with a security warning about risks around opening attachments or executing downloaded files. Ignoring the warning and continuing the download leads to the installation of malware.
Key Action: Report Suspicious Emails
- Report ANY suspicious emails using the Phish Alarm button in your email menu bar.
- Remember: Our organization occasionally sends phishing simulations that are used to evaluate the potential impact of a real phishing attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Keep in mind that cybercriminals regularly abuse legitimate services like OneNote. This may allow cybercriminals to send malicious emails from legitimate sending addresses. If you see an unexpected email linking you to an unknown document, it should be regarded as potentially malicious.
- Verify the legitimacy of any unsolicited/unexpected email before you interact with it, especially if it directs you to click on a link. It can be tempting to click on a “call-to-action.” But if you notice a subtle change or inconsistency within a message, don’t ignore it—report it.
- Verify attachments, even if they’re sent through or posted to an internal cloud system or messaging platform. It’s possible for internal accounts to be compromised. In these cases, messages and posts from legitimate employees will have malicious intent. These are very hard to spot, but your attention to detail can help.