This content is viewable by Everyone
Jan 2025: LEGITIMATE GOOGLE Infrastructure Used in Google Support Spoofing
Threat Alert: LEGITIMATE GOOGLE Infrastructure Used inGoogle Support Spoofing
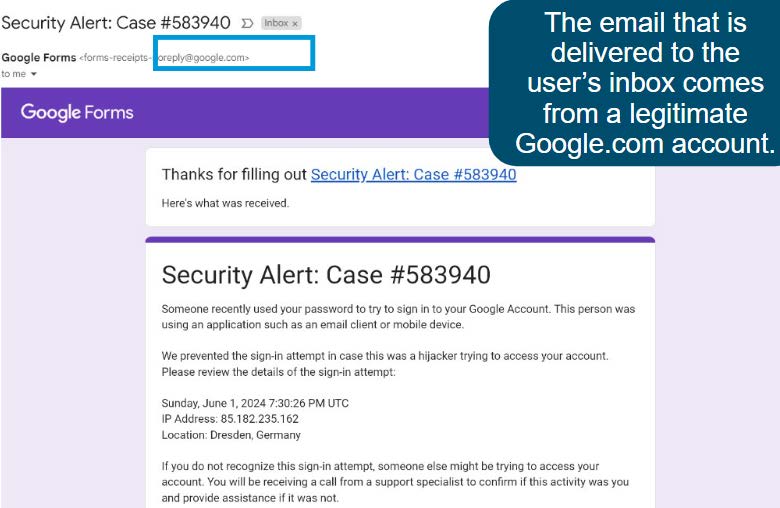
- Proofpoint Threat Intelligence Service (PTIS) identified a series of phishing emails spoofing Google Support using legitimate Google infrastructure.
- Attackers create a Google Form mimicking a Google security alert. By entering a target’s email address in the form, the target receives a copy of the form from a legitimate Google address.
- Attackers then call the target from a legitimate Google-owned number by using Google AI Assistant.
- The attacker can then guide the target through the account recovery process, which ultimately gives the attacker access to the target’s Google account.
Key Action: Report Suspicious Emails
- Keep in mind that cybercriminals regularly abuse legitimate services. Abusing legitimate services gives cybercriminals and their lures an additional air of legitimacy.
- Do not answer calls from unknown numbers. In general, this is the easiest way to avoid voice phishing (vishing) attacks. Remember, attackers can exploit legitimate services to make their call appear legitimate.
- Report ANY suspicious emails received in your UCSF email box using the Phish Alarm button.