This content is viewable by Everyone
Jul 2023: Phishing Attacks Use Fight-Themed Lure to Spread Malware
Threat Alert: What to Watch For
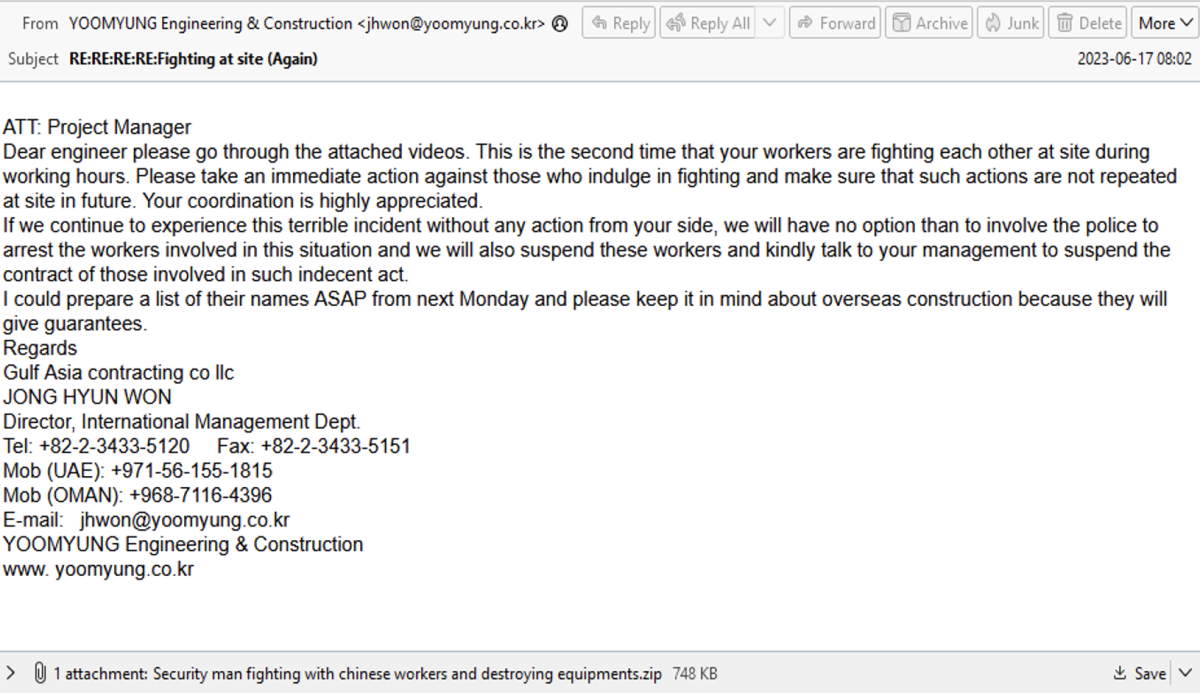
- Cybercriminals have launched a series of phishing attacks that claim to inform the recipient of physical altercations between employees and equipment damage at a worksite.
- The lures include a malicious attachment allegedly containing a video of the altercation. If opened, the attachment downloads malicious software onto the device.
- These lures also threaten police action if the recipient does not take action against the workers allegedly shown in the video.
Key Action: Report Suspicious Emails
- Report ANY suspicious emails using the Phish Alarm button in your email menu bar.
- Remember: Our organization occasionally sends phishing simulations that are used to evaluate the potential impact of a real phishing attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Beware of content that causes strong emotions. Cybercriminals look for ways to increase pressure on recipients of phishing emails. Threats of police action are intended to increase the chances of interaction with malicious attachments or URLs.
- Verify the legitimacy of any unsolicited/unexpected email before you interact with it, especially if it directs you to download an attachment. If you notice a subtle change or inconsistency within a message claiming to be from a third-party organization, don’t ignore it—report it.
- Confirm via a secondary means of communication. If an email seems off or is asking for you to immediately open a link or attachment, confirm the legitimacy of the email via a known, secondary means of communication — like a known, trusted phone number. Do not rely on alternate means of communication supplied in the email itself.