This content is viewable by Everyone
Jul 2024: CrowdStrike-Themed Lures Lead to Malware and Credential Theft
Threat Alert: CrowdStrike- Themed Lures Lead to Malware and Credential Theft
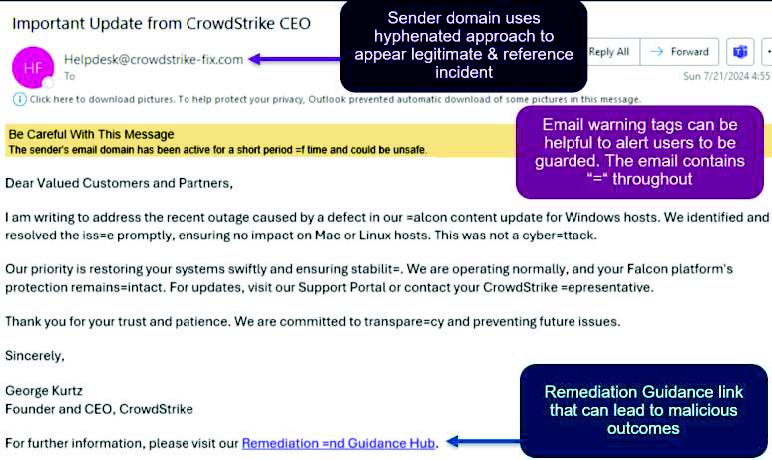
- Phishing attacks leveraging the recent Microsoft IT outage caused by CrowdStrike’s production incident have been identified.
- The lures allegedly come from CrowdStrike’s CEO George Kurtz and come from the sender domain helpdesk[@]crowd- strike-fix[.]com.
- Within the lures are a link to a purported remediation guidance hub for organizations impacted by the incident.
- Following the link may ultimately lead to the installation of malicious software (malware) or credential theft.
Key Action: Report Suspicious Emails
- Remain alert to phishing indicators. Mismatches between sending addresses and an organization’s name are always warning signs, as are frequent typos, grammatical mistakes, or alphanumeric substitutions, such as replacing the letter “O” with “=”.
- Remember that cybercriminals commonly leverage current events in phishing attacks. Major stressful events, such as a global IT outage, give attackers ample material for sending out phishing lures.
- Report ANY suspicious emails using the Phish Alarm button.