This content is viewable by Everyone
Jul 2025: DISGUISED SIMPLEHELP THREAT ZOOM LURE
Threat Alert: DISGUISED SIMPLEHELP THREAT ZOOM LURE
- SimpleHelp and other remote monitoring and management (RMM) tools are often abused by threat actors due to their robust capabilities, trusted status, and ability to blend in with legitimate activity.
- According to security research, multiple prominent threat actors, including DragonForce and Play Ransomware, have recently used RMM to deploy ransomware
in victim environments.
How is it used in the wild?
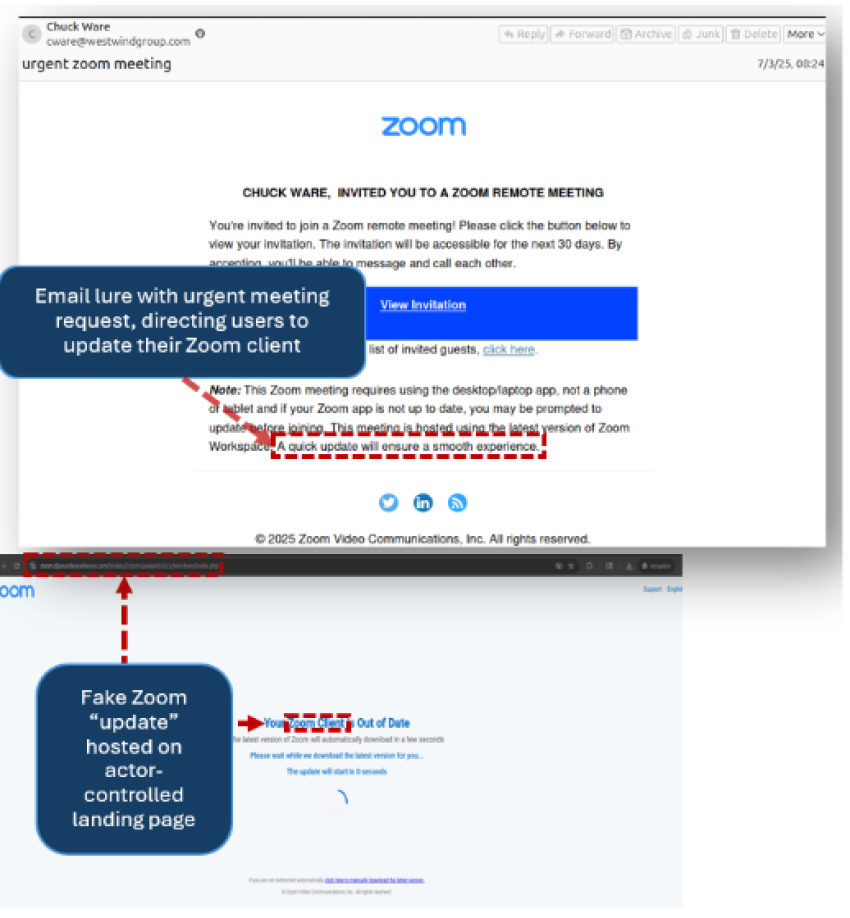
- Using compromised email accounts, threat actors distribute emails with fake invitations to Zoom meetings and urge users to update Zoom instances to avoid technical issues.
- Threat actors attempt to elicit interaction from recipients by using subject lines that purport to lead to important and potentially lucrative business opportunities.
- If the URLs in the message body are selected, the RMM tool SimpleHelp is installed on victim endpoints.
- Once installed, threat actors can then conduct remote operations, gather information about the victim environment, and deploy additional payloads, including ransomware.
Key Action: Stay Alert!
- Be suspicious of unsolicited messages from external senders: Be wary of messages that try to make you engage in new business ventures and/or perform updates to software or applications.
- Scrutinize the details of email messages and any external websites you are directed to from unsolicited messages.
- Report ANY suspicious emails via Phish Alarm.