This content is viewable by Everyone
Jul 2025: EMPLOYEE BENEFITS HR LURES - CREDENTIAL PHISHING
Threat Alert: EMPLOYEE BENEFITS HR LURES - CREDENTIAL PHISHING
- Threat actors consistently impersonate Human Resources (HR) to pressure users to interact with malicious materials.
- Previously concentrated during the New Year, threat actors are now sending waves of corporate communication-themed threats around the beginning of every quarter.
How is it used in the wild?
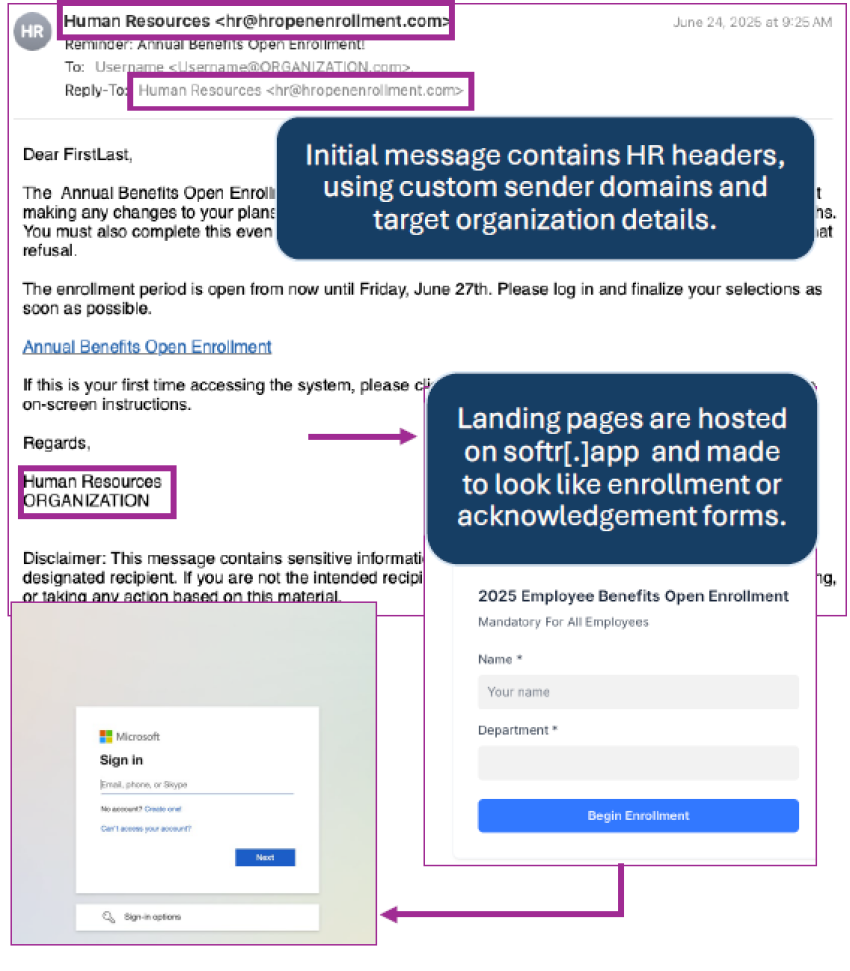
- Recently observed threats purport to deliver notifications regarding open enrollment and new company policies using spoofed headers and email addresses.
- These threats contain URLs, usually hosted on recently created domains (within the last 30 days), that lead to employee confirmation pages. They use automation to populate target details like name and target organization.
- Landing pages contain “View Report” or “Begin Enrollment” hyperlinks that lead to credential harvesters.
- Filing the fields and clicking the link in the intermediate form leads to an O365 credential harvester.
Key Action: Stay Alert!
- Be suspicious of unsolicited messages from external senders: interrogate headers and browser address bars for spoofed senders and lookalike domains.
- Use a trusted bookmark to log into accounts instead of following links in unsolicited emails.
- Report ANY suspicious emails via Phish Alarm.