This content is viewable by Everyone
Jul 2025: MICROSOFT “POLICY VIOLATION” LURE - CONSENT PHISHING ATTACK
Threat Alert: MICROSOFT “POLICY VIOLATION” LURE - CONSENT PHISHING ATTACK
- Consent phishing attacks aim to trick users into granting permission to the Threat Actor, giving the adversary access to users’ accounts and legitimate cloud services.
- Malicious purposes for threat could include backdoors, phishing, cryptocurrency mining, or launching spamming campaigns using the targeted organization’s resources and domain name.
How is it used in the wild?
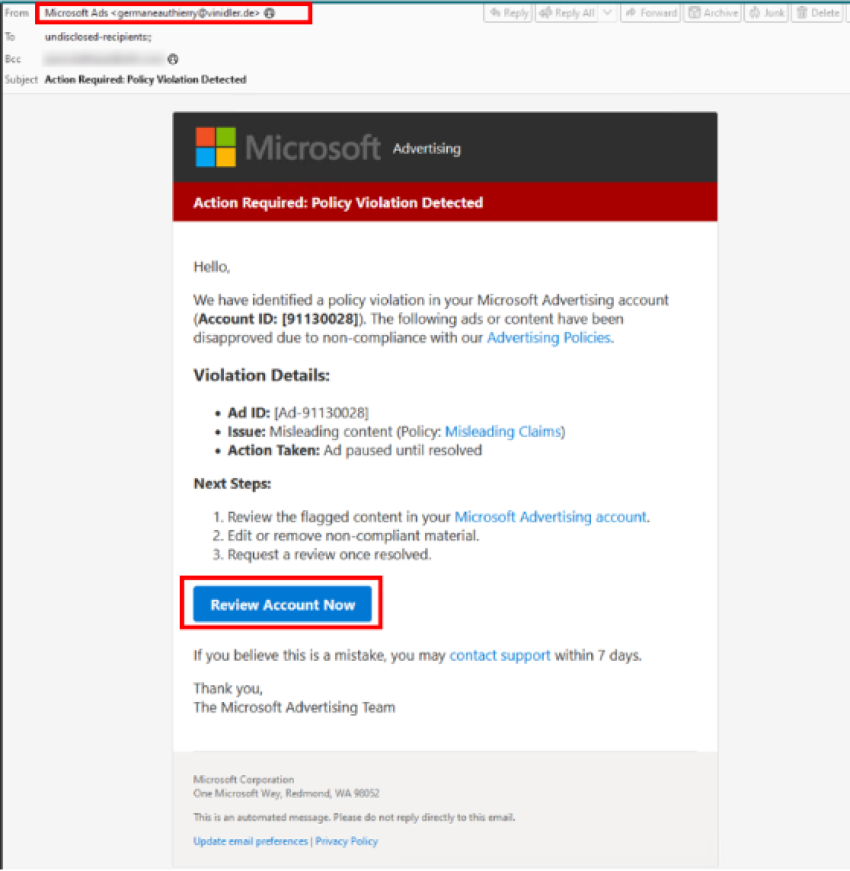
- Messages claim to come from Microsoft Ads with a Subject Line of “Action Required: Policy Violation Detected.”
- Messages were delivered by a non-Microsoft account and contained a URL to a landing page with an immediate redirect to https://ads-microsoflt[.]site, a typo-squatted or counterfeit domain very similar to the legitimate https://ads.microsoft[.]com.
- Once on the counterfeit “Microsoft Ads” website, the end user is requested to sign in to their Microsoft account. If successful, this would compromise the victim’s account.
Key Action: Stay Alert!
- Be suspicious of unsolicited messages from external senders: Investigate sender information, and use a trusted bookmark to log into accounts instead of following links in emails.
- Report ANY suspicious emails via Phish Alarm.