This content is viewable by Everyone
Jun 2025: CREDENTIAL & QR CODE PHISHING WITH A PAYROLL LURE
Threat Alert: CREDENTIAL & QR CODE PHISHING WITH A PAYROLL LURE
- Credential phishing threats often use various attachments to bypass detection and socially engineer recipients to harvest credentials.
- Tactics involve threat actors prompting users to click on multiple attachments, adding layers to a social engineering attempt.
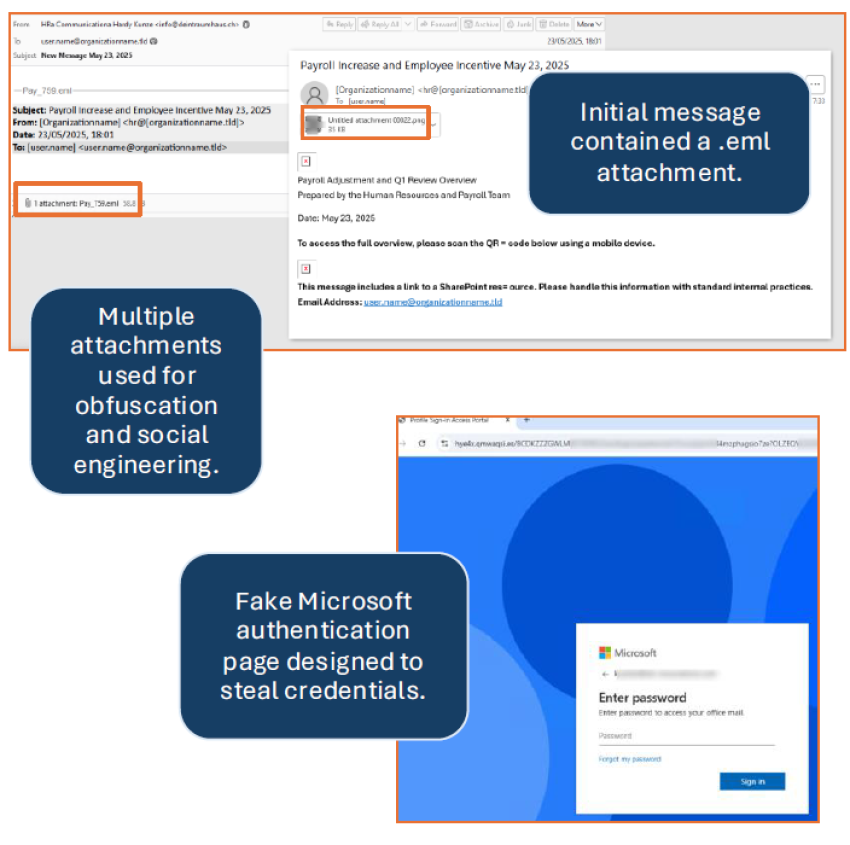
- This threat includes an adversary-in-the-middle (AitM) credential phishing campaign that used multiple attachment types to lead to a QR code phishing threat.
How is it used in the wild?
- This phishing campaign begins with an email claiming to be from the recipient’s HR department about a payroll adjustment.
- The message body highlights header information from a separate email and includes an .eml attachment.
- The .eml attachment contains a message about the payroll adjustment and prompts access to a .png attachment.
- Both email messages include personalization to enhance engagement legitimacy.
- The .png file contains a QR code that directs to a fake Microsoft page intended to steal credentials, including 2FA tokens and session cookies, through AitM capabilities.
Key Action: Stay Alert!
- Be cautious with .eml attachments and QR codes from unsolicited or suspicious sources. These can deliver malicious content. Avoid opening them unless you're sure of the source.
- Stay alert with .png files. They may contain malicious QR codes directing you to harmful websites.
- Watch for suspicious behavior from contacts. If someone sends unusual messages, links, or uses unfamiliar language, their account may be compromised.
- Verify unexpected notifications from HR by contacting your HR representative directly.
- Report ANY suspicious emails via Phish Alarm.