This content is viewable by Everyone
June 2023: Phishing Attacks Abuse Valid Web Traffic Tool
Threat Alert: What to Watch For
- Cybercriminals have launched phishing attacks abusing legitimate tools that are used to direct web traffic.
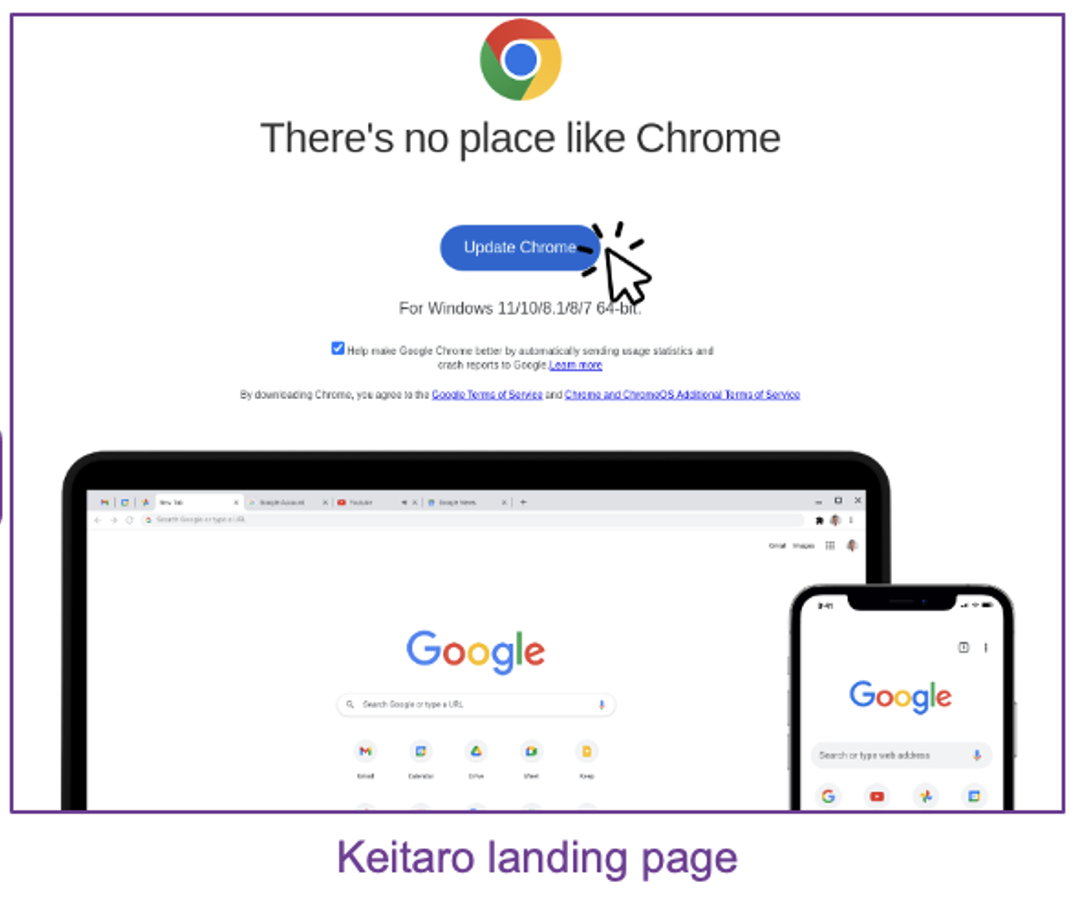
- Phishing lures contain an embedded URL that leads to a lookalike Google Chrome update site.
- Downloading the fake Google Chrome update installs a legitimate tool used for remotely monitoring and supporting computers. Attackers then abuse this tool to take control of the device to steal data or use the infected device for further malicious actions.
Key Action: Report Suspicious Emails
- Report ANY suspicious emails the Phish Alarm button in your email menu bar.
- Remember: Our organization occasionally sends phishing simulations that are used to evaluate the potential impact of a real phishing attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Go beyond surface clues. Familiar logos, branding, and names are not automatic indicators that an email or website is safe. Cybercriminals often imitate well-known organizations.
- Be aware of potential lookalike web pages. When downloading software from the internet, always look for signs of potential web page impersonation. Be sure to check the URL carefully. Some imposter sites use URLs that very closely resemble the legitimate URL.
- Do not download or update software strictly based on a web-based pop-up notification or email alert. Fake notifications are persistently used by malware distributors to pressure targets into a download. System alerts should originate from native tools, not from browser pop-ups or webpages.
- Follow approved software installation processes. If you need to download or update a specific software utility or application, follow organization-specified processes or reach out to a member of the technology or security team for help.