This content is viewable by Everyone
Mar 2023: Malicious OneNote Attachment Lures
Threat Alert: What to Watch For
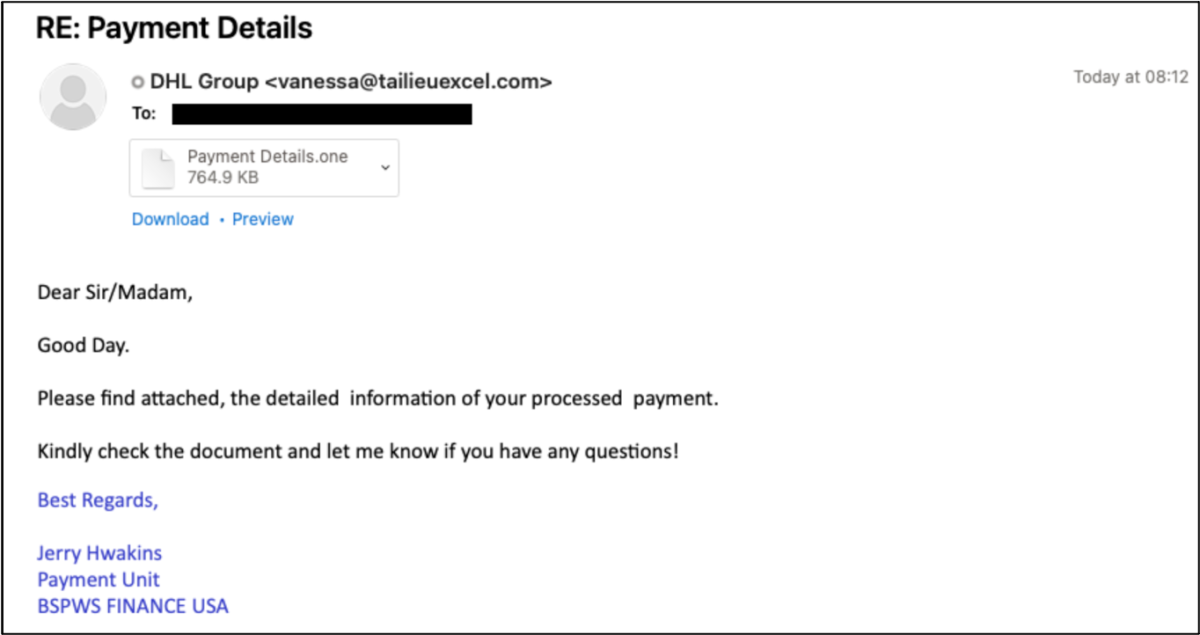
- Recent email-based attacks have abused Microsoft’s legitimate OneNote application to share malicious files. The emails include attached files with titles such as “Payment Details.one” and encourage the recipient to follow a link to view a shared OneNote file.
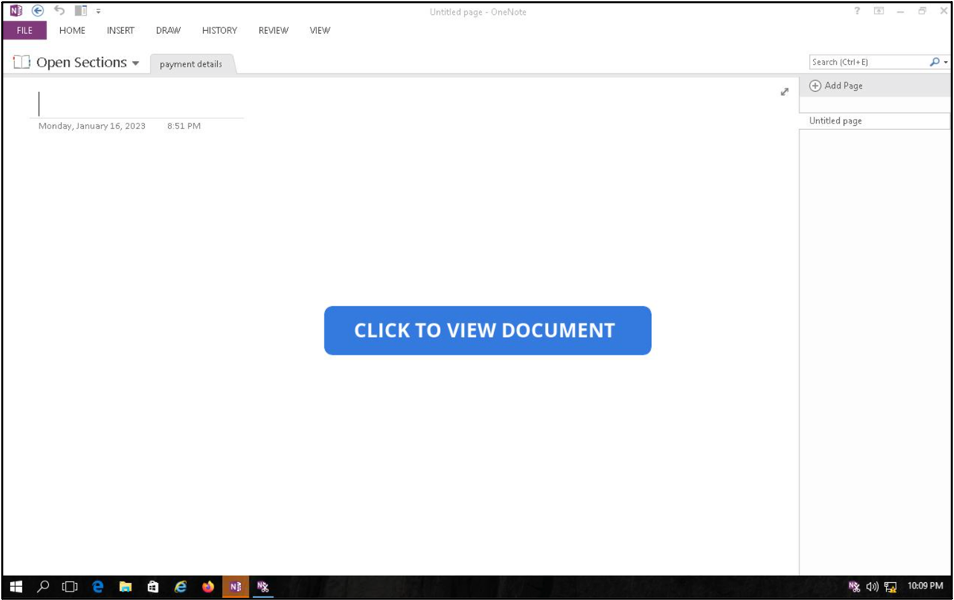
- The OneNote link leads recipients to a shared document containing a prompt to click an embedded link to view an additional file.
- Some attacks may also distribute similar malicious OneNote files as URLs.
- High-profile employees often have email addresses that are widely available, making it easy for threat actors to target them. Be wary of unknown or unexpected emails to these accounts.
Key Action: Report Suspicious Emails
- Report ANY suspicious emails using the Phish Alarm button in your email menu bar.
- Remember: Our organization occasionally sends phishing simulations that are used to evaluate the potential impact of a real phishing attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Go beyond surface clues. Familiar logos, branding, and names are not automatic indicators that an email or website is safe. Cybercriminals often imitate well-known organizations.
- Verify the legitimacy of any unsolicited/unexpected email before you interact with it, especially if it directs you to click on a link or asks you to provide credentials. It can be tempting to click on a “call-to-action.” But if you notice a subtle change or inconsistency within a message, don’t ignore it—report it.
- Confirm ANY payment requests before acting on them. Fraudulent payment requests are common. Any email that instructs you to pay an invoice, execute a wire transfer, or complete a purchase should be verified through approved procedures—especially if the message is unexpected or unusual.
- Remain alert to attacks targeting Executives and other VIPs. VIPs, executives, and privileged users are popular targets for credential theft and malware campaigns as many have privileged access to accounts or data.