This content is viewable by Everyone
Mar 2025: CRITICAL UPDATES “REQUIRED” LURE
Threat Alert: CRITICAL UPDATES “REQUIRED” LURE
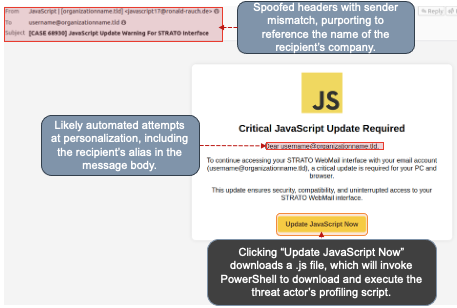
- A post-exploitation threat actor is working to deliver a JavaScript-based profiling script disguised as a ”Critical JavaScript Update.”
- The threat actor hires, partners, or works with other threat actors to distribute payloads.
- This threat is part of a larger, notable trend where a growing variety of threat actors across the landscape use lures obfuscating malware as updates to known and trusted software applications.
How is it used in the wild?
- Malicious messages with spoofed email headers are sent to targets. These messages often appear as communications from internal IT departments regarding a software update.
- The message’s body contains a well-constructed lure that claims to link to a “Critical JavaScript Update Required” and includes the recipient's address in the content.
- Automated personalization techniques are likely used to include the recipient’s address in message body content, giving the appearance of a “targeted” attack.
- If “Update JavaScript Now” is clicked, it triggers the download of a JavaScript file. PowerShell will pull down and install the threat actor’s profiling script if executed.
Key Action: Stay Alert!
- Examine email headers to identify any mismatches, a common sign of malicious mail.
- Understand the official internal communications regarding security, software, and other issues.
- Stay alert for signs of fake or automated “personalization,” including using your email address in subject lines and message bodies.
- Report ANY suspicious emails via Phish Alarm.