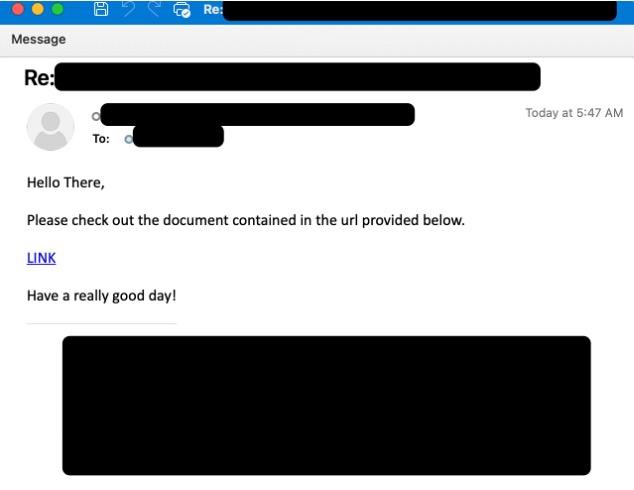
This content is viewable by Everyone
May 2023: Phishing Attacks Deliver Remote Access Malware
Threat Alert: What to Watch For
- Cybercriminals have launched phishing attacks using a variety of lures to spread a Remote Access Trojan (RAT), which is a type of software that grants attackers access and control over an affected computer.
- Lures used in these attacks include impersonation of seen DHL in reference to an undelivered package, as well as emails making vague references to shared documents.
- Some of the phishing attacks hijack legitimate email threads to deliver the phishing lures to further increase the believability of the attacks. This means the lures may appear to be responses to previous, legitimate email conversations.
- All lures in this attack include a link that, when clicked, leads to a blank webpage that automatically downloads a JavaScript file. Running the file leads to the installation of the RAT.
Key Action: Report Suspicious Emails
- Report ANY suspicious emails using the Phish Alarm button in your email menu bar.
- Remember: Our organization occasionally sends phishing simulations that are used to evaluate the potential impact of a real phishing attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Go beyond surface clues. Familiar logos, branding, and names are not automatic indicators that an email or website is safe. Cybercriminals often imitate well-known organizations.
- Email replies from trusted accounts can be malicious. Some phishing attacks will compromise legitimate accounts and respond to conversations to appear more believable. Always be sure to verify the legitimacy of unexpected URLs from trusted sources through a different means of communication, like a phone call or in person.
- Be cautious of clicking on URLs, particularly in unsolicited emails or if they seem out of character for a known sender. Instead, always navigate to a website directly through a known URL or a trusted bookmark.