This content is viewable by Everyone
May 2025: NHS & Medicare Lure Spoofing to ScreenConnect
Threat Alert: NHS & Medicare Lure Spoofing to ScreenConnect
- Threat actors are spoofing the United Kingdom’s National Health Service (NHS) and Australia’s Medicare in attempts to deliver ScreenConnect.
- ScreenConnect is legitimate Remote Monitoring and Management (RMM) software frequently abused by cybercriminals for various malicious purposes.
- Lures spoofing government and medical agencies are common and increasing in use, likely driven by the increased public focus on public benefit programs.
How is it used in the wild?
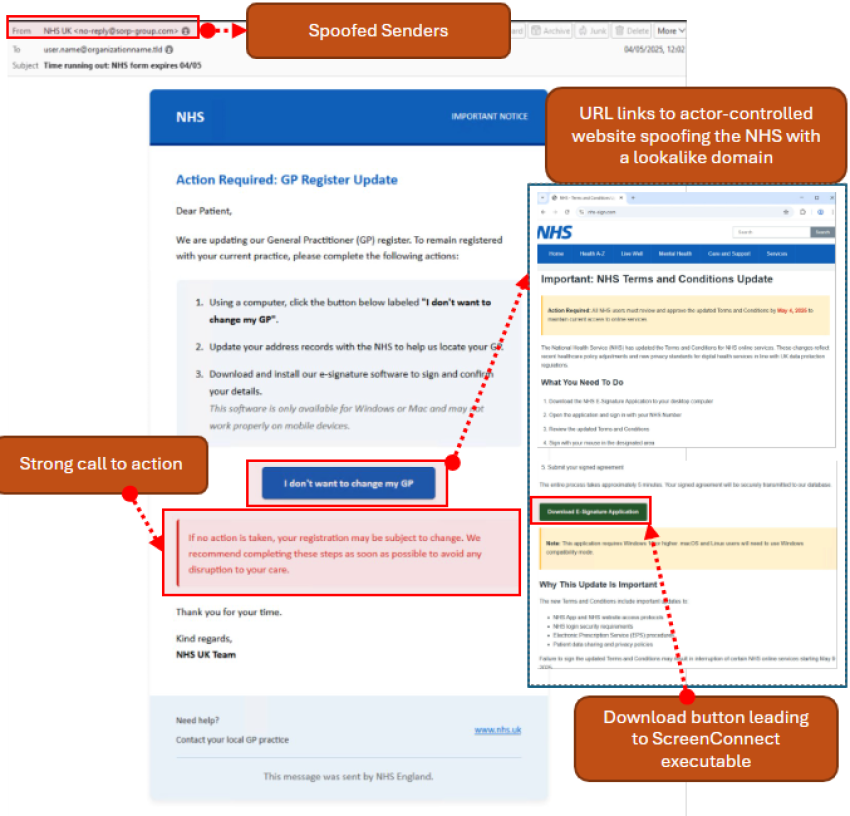
- Observed activity includes a variety of lures, including the following examples:
- Acknowledge a change in terms and conditions.
- Register for paperless or digital services.
- Update General Practitioner (GP) information or confirm no change in information.
- All messages include a box with an embedded URL that directs to an actor, designed to imitate the authentic websites of the NHS (UK) and Medicare (AUS).
- Malicious websites contain instructions to download a file to complete the purported task.
- The file is a malicious ScreenConnect executable that, if installed, will grant the threat actor access to the victim’s endpoint.
Key Action: Stay Alert!
- Go beyond surface clues. Familiar logos, branding, and names are not automatic indicators that an email or website is safe. Cybercriminals regularly imitate medical and government agencies.
- Remain alert to phishing indicators. Interrogate headers and browser address bars for spoofed senders and look-alike domains.
- Log into accounts independently and never navigate to login pages from unsolicited emails. Use a trusted bookmark or type the URL to the legitimate website into the address bar.
- Report ANY suspicious emails via Phish Alarm.