This content is viewable by Everyone
Nov 2022: Amazon-Themed Lures Distributed Via Zoom
Threat Alert: What to Watch For
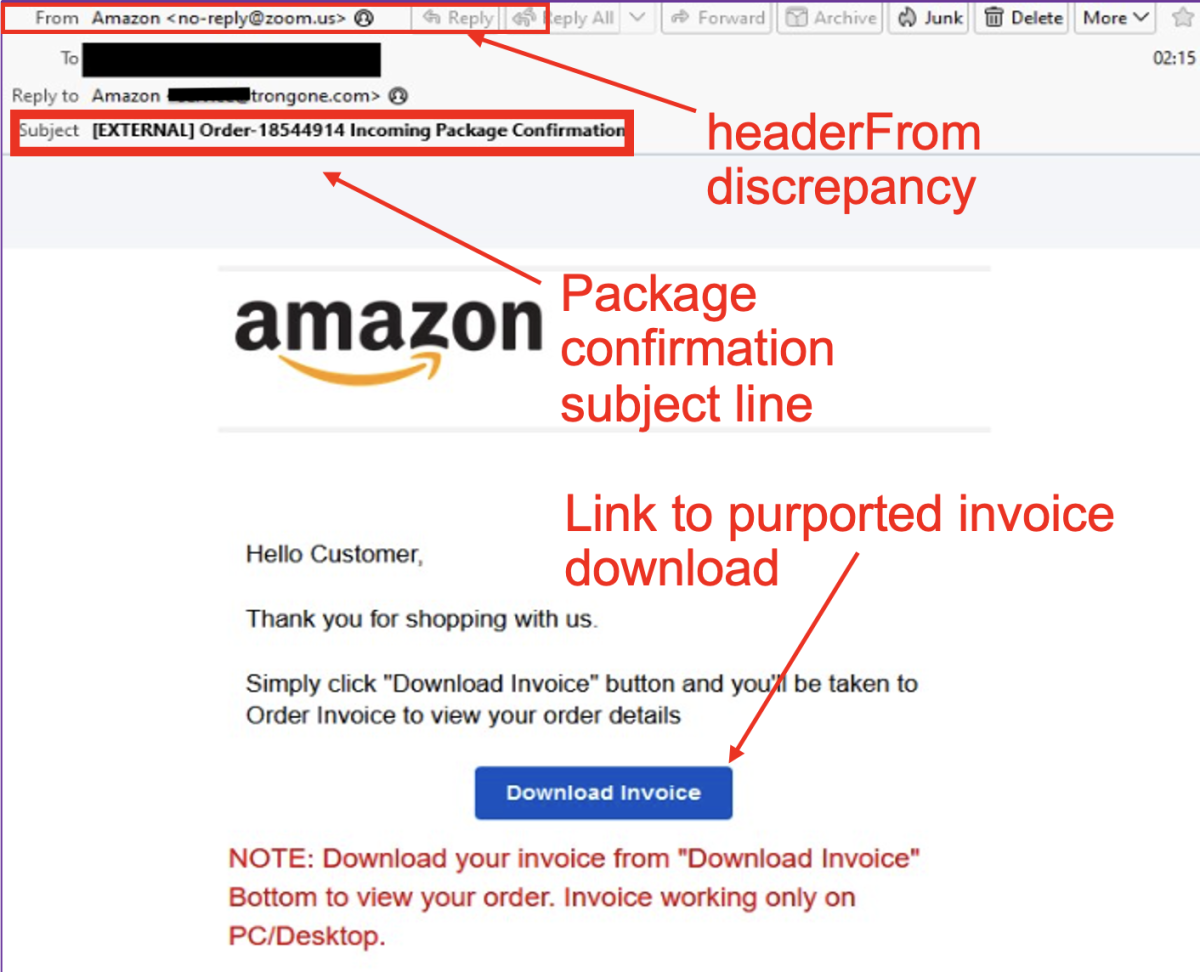
- Cybercriminals have launched a series of malicious email attacks impersonating an Amazon package order confirmation.
- The attack uses Amazon-branded emails delivered from a Zoom sending address, as threat actors are abusing Zoom’s infrastructure.
- The emails prompt recipients to click a link to download an invoice for order details. Doing so could result in in the installation of malicious software (malware) on a recipient’s device.
Key Action: Report Suspicious Emails
- Report ANY suspicious emails by clicking on the Phish Alarm button.
- Remember: Our organization occasionally sends malicious email simulations that are used to evaluate the potential impact of a real attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Go beyond surface clues. Familiar logos, branding, and names are not automatic indicators that an email is safe. Cybercriminals often imitate well-known organizations.
- Verify the legitimacy of any unsolicited/unexpected email before you interact with it, especially if it directs you to click on a link or download a file. If in doubt, always navigate directly to a company’s trusted webpage to check items like order status.
- Keep in mind that cybercriminals regularly abuse legitimate services like Zoom. This may allow them to send malicious emails from legitimate sending addresses. If you see an organizational email delivered from a different company’s sending address, it should be regarded as potentially malicious.