This content is viewable by Everyone
Nov 2022: Twitter-Themed Lures Used in Credential Phishing Attacks
Threat Alert: What to Watch For
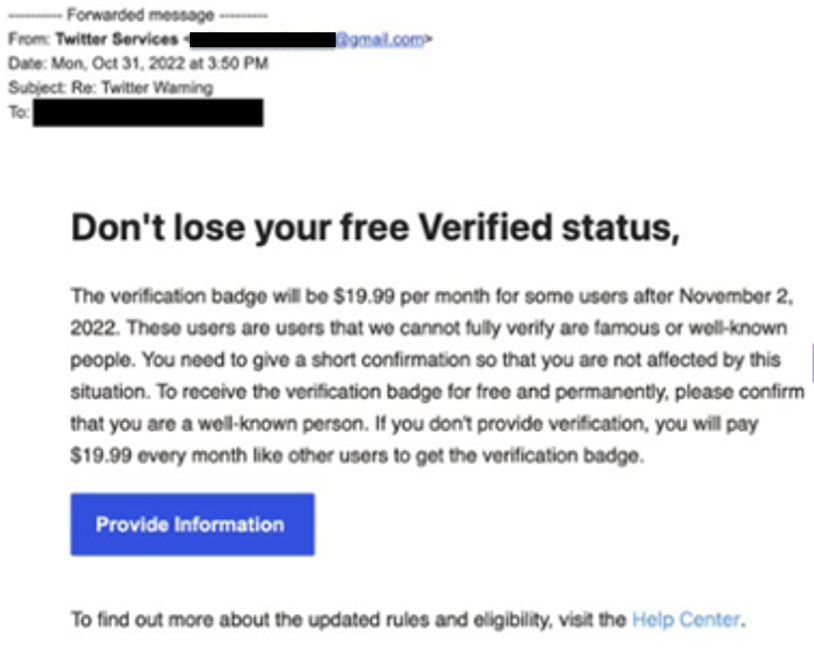
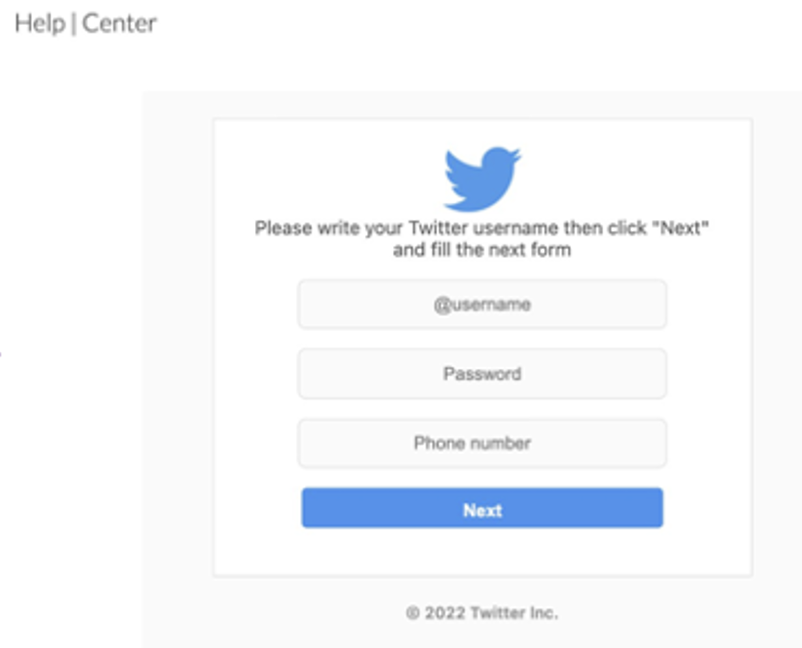
- Cybercriminals have launched phishing attacks impersonating Twitter Services. The emails include links to lookalike landing pages that are designed to steal Twitter credentials and phone numbers.
- While the email display names make it appear the messages come from “Twitter Services,” the actual sending address is a Gmail account.
- The emails use the proposed change at Twitter of charging verified users a monthly fee to maintain their verification status. The messages try to entice recipients into clicking a link in the email by promising to provide account verification for free.
- While these attacks reference the much-discussed “blue check” controversy at Twitter, any unsolicited emails that appear to come from Twitter in the next several weeks or months should be handled with caution. Additionally, you should be cautious of unsolicited direct messages on Twitter, especially those encouraging you to continue the conversation on another platform.
Key Action: Report Suspicious Emails
- Report ANY suspicious emails by clicking on the Phish Alarm button.
- Remember: Our organization occasionally sends malicious email simulations that are used to evaluate the potential impact of a real attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Remember that cybercriminals commonly leverage current events in phishing attacks. High-profile news events like the ongoing changes at Twitter spark a lot of curiosity and conversation. Attackers know people will be tempted to engage with emails that mention these kinds of topics, especially when offering the opportunity to obtain a premium service for free.
- Be extremely cautious of emailed links that lead you to an account login page—even if the page looks “right.” It’s always safest to control your own path and log in via known, trusted channels.
- Remain alert to phishing indicators. Mismatches between sending addresses and an organization’s name are always warning signs (Twitter would never send an email from a Gmail account!).