This content is viewable by Everyone
Nov 2025: AI-GENERATED CONTACT FORMS
Threat Alert: BENEFIT ELECTION ACCOUNT COMPROMISE
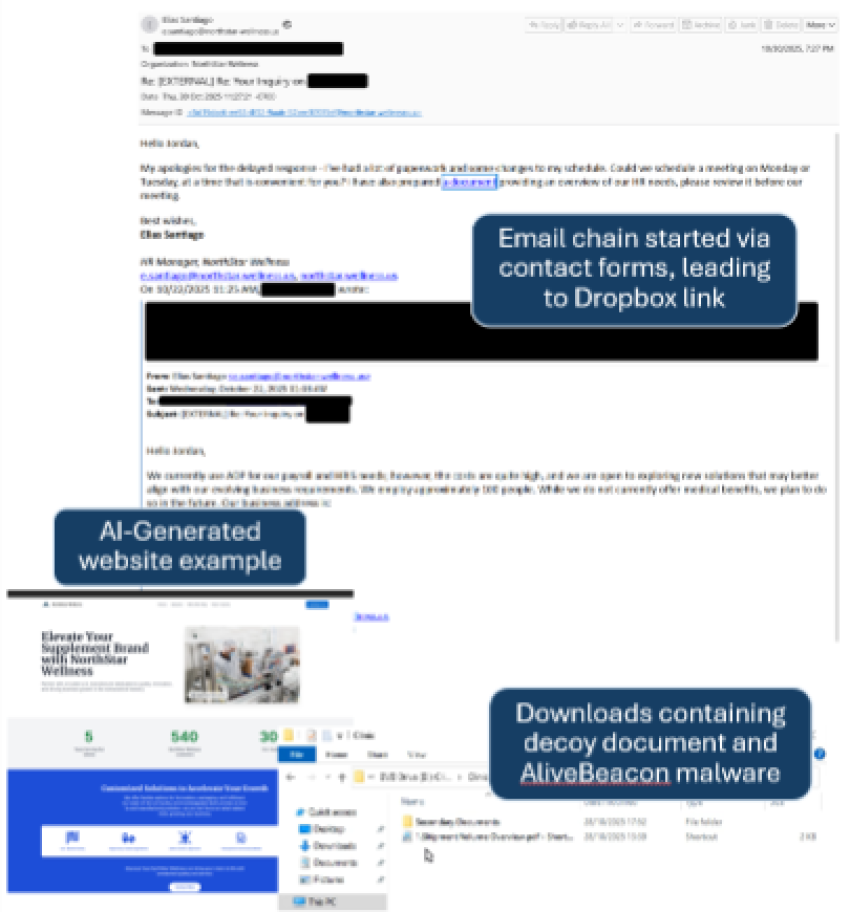
- Threat actors create impersonation websites or fake company domains, then use contact forms to start conversations with targets. Once they receive a response, they send the target files that lead to decoy documents and a new form of malware.
- The actors use AI-generated content in emails, documents, and websites to make their communications more convincing.
How is it used in the wild?
- Threat actors create fake business domains or clone existing websites to establish a seemingly legitimate business presence.
- Actors initiate contact through contact forms to purportedly elicit business and engage in social engineering conversations to build trust with the targets.
- After establishing contact, the actor sends Dropbox links that contain decoy and malicious files that execute an obfuscated PowerShell script.
- The script downloads a new malware, AliveBeacon, which is a backdoor that establishes persistence and periodically
polls command and control (C2) infrastructure for commands.
Key Action: Stay Alert!
- Keep in mind that cybercriminals regularly abuse legitimate services like Dropbox. Abusing legitimate services gives cybercriminals and their lures an additional air of legitimacy.
- If you see an unexpected email linking you to Dropbox, it should be regarded as potentially malicious.
- Always verify new business contacts through alternative channels.
- Report ANY suspicious emails via Phish Alarm.