This content is viewable by Everyone
Nov 2025: BENEFIT ELECTION ACCOUNT COMPROMISE
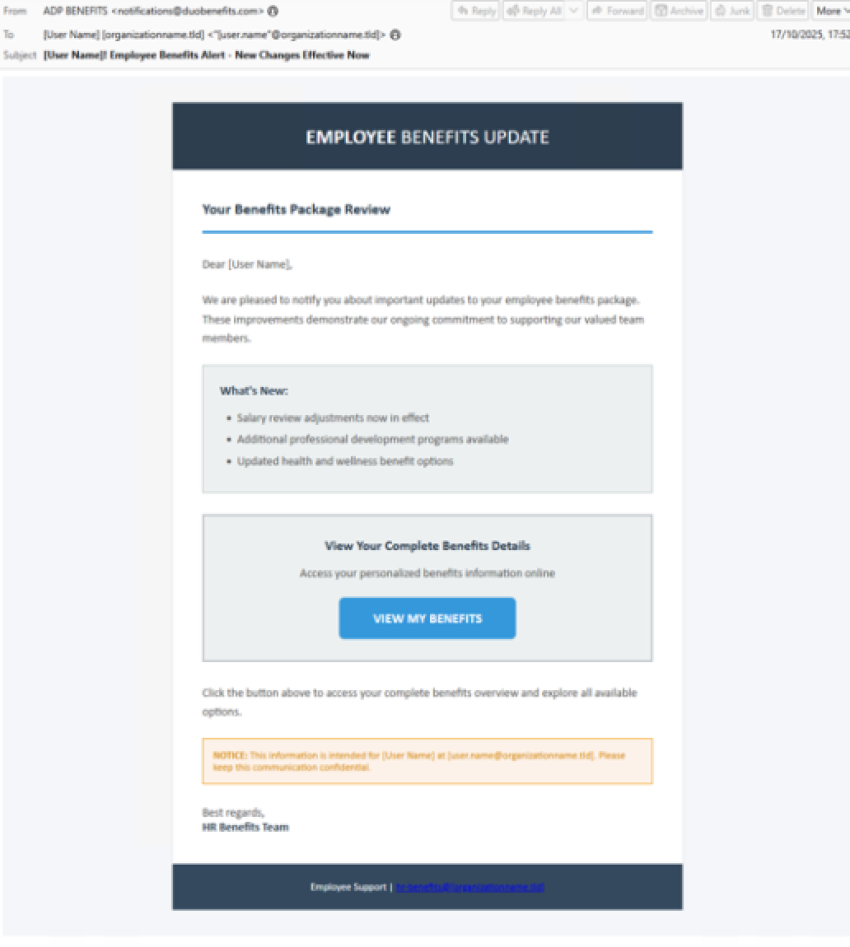
Threat Alert: BENEFIT ELECTION ACCOUNT COMPROMISE
- Threat actors sent messages purporting to
be from “ADP Benefits” and claiming that changes were made to the recipient’s
benefits, including salary, education, and health benefits. - This follows the trend of threat actors leveraging HR-related lures toward the end of the year, as employees are expecting to receive such notices from their employers.
How is it used in the wild?
- Threat actors sent messages with the subject “Employee Benefits Alert – New Changes Effective Now”.
- The message body contained a link that led to a Microsoft or Okta branded adversary-in-the-middle (AitM) phishing page which harvested end user credentials, multi-factor authentication (MFA), and session cookie data.
- If completed, the page would send the information to the threat actor, who could then authenticate to the account.
Key Action: Stay Alert!
- Keep an eye out for seasonal trends related to threat actors, in this case focusing on end-of-year, HR-related themes.
- Know where legitimate UCSF HR-related comms will come from, so you have a baseline to compare potentially anomalous traffic to.
- Make a practice of scrutinizing message headers for spoofed senders. And be wary of messages that elicit an emotional response, such as notifications around salary.
- Report ANY suspicious emails via Phish Alarm.