This content is viewable by Everyone
Oct 2023: Dual-Purpose Phishing Attacks Use Blocked Email Lure
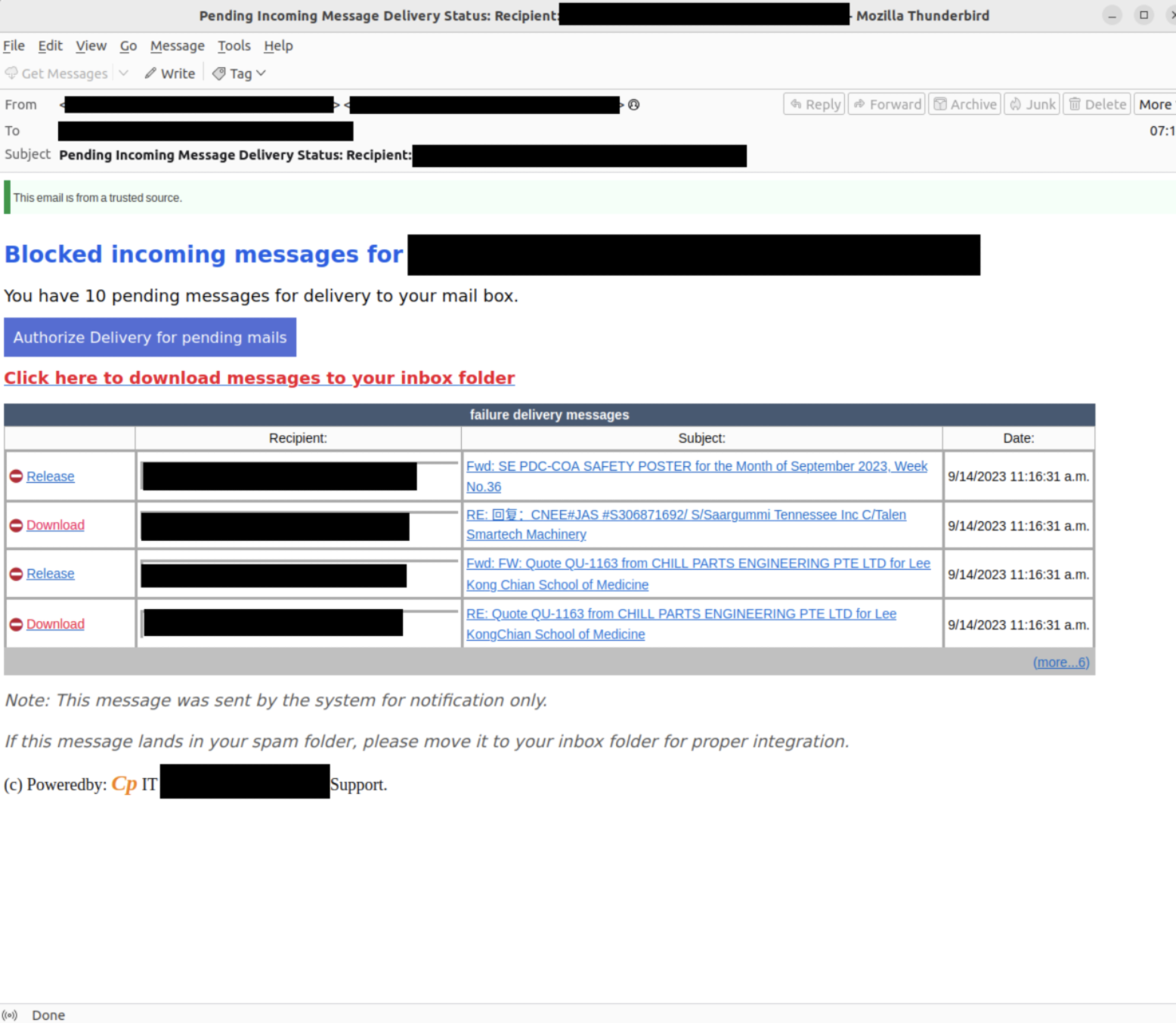
Threat Alert: Dual-Purpose Phish Use Blocked Email Lure
- Cybercriminals have launched a series of phishing attacks impersonating the recipient’s IT support team.
- The emails include the recipient’s name in the subject line and message body to increase the appearance of legitimacy.
- The phishing attacks use a lure detailing allegedly blocked inbound messages for the recipient.
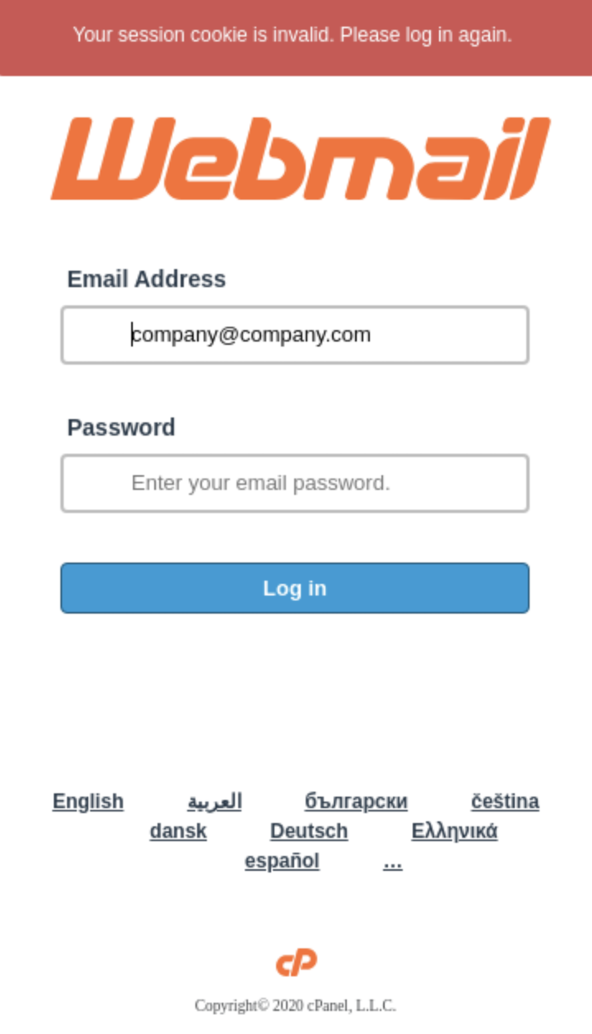
- The lures contain multiple malicious URLs, some of which lead to a lookalike cPanel email authentication page and some of which lead to the installation of malicious software (malware) contained in a malicious .zip file.
Key Actions (at Work and at Home)
- Verify the legitimacy of any unsolicited/unexpected email before you interact with it, especially if it directs you to click on a link or asks you to provide credentials. It can be tempting to click on a “call-to-action.” But if you notice a subtle change or inconsistency within a message claiming to be from IT or another internal department, don’t ignore it—report it.
- Be cautious of clicking on URLs, particularly in unsolicited emails or if they seem out of character for a known sender. Instead, always navigate to a website directly through a known URL or a trusted bookmark.
- Report ANY suspicious emails using the Phish Alarm button