This content is viewable by Everyone
Oct 2025: FAKE UNITEDHEALTHCARE ALERTS
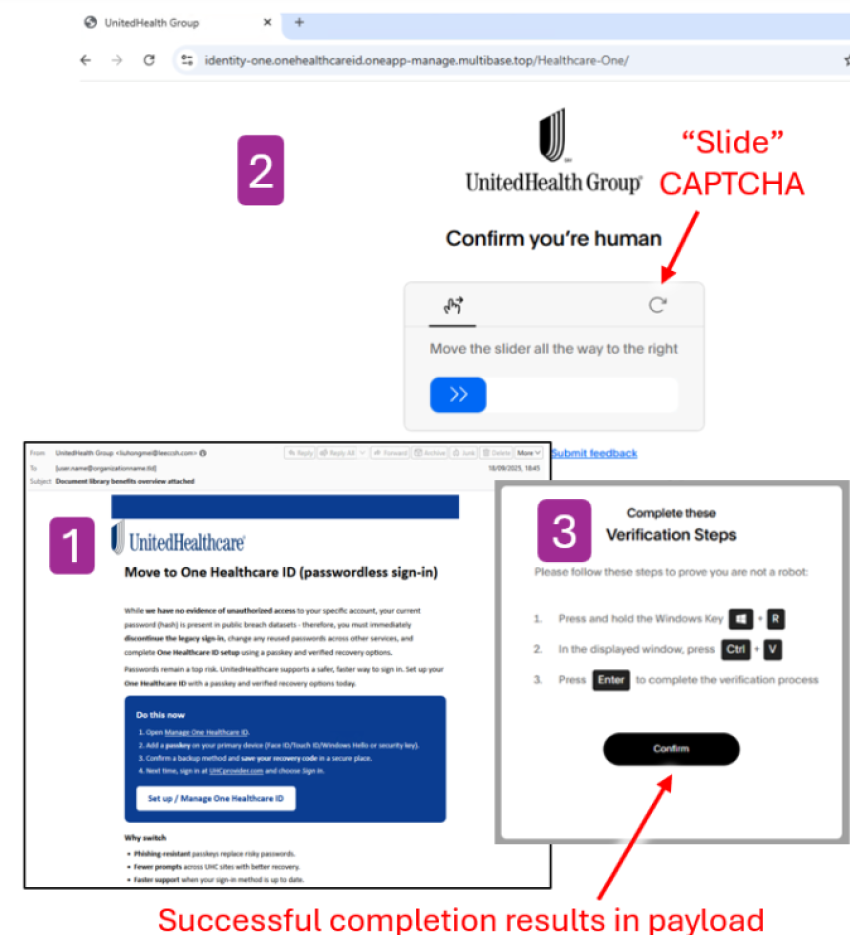
Threat Alert: FAKE UNITEDHEALTHCARE ALERTS
- fake UnitedHealthcare Group sender domains, landing pages, and misuse of legitimate branding. Successful attacks resulted in a ClickFix landing page with XWorm and SharpHide payloads.
- UnitedHealthcare Group is active in news reporting and social media, providing ample opportunities for threat actors to craft timely, urgent, and credible lures.
How is it used in the wild?
- Messages are from various senders impersonating the UnitedHealthcare Group or CareerBuilder and include a link to a matching themed landing page with a “Slide” CAPTCHA.
- If the CAPTCHA is resolved, a ClickFix landing page instructs users to run Windows PowerShell and copy and paste a string of code. This results in the download and deployment of XWorm or SharpHide.
- XWorm can establish a foothold in the system and pave the way for future malware and/or ransomware. SharpHide is a WhiteHat tool that can hide malicious entries from the Windows Registry Editor. Both give threat actors persistence across system reboots and the ability to deploy additional payloads.
Key Action: Stay Alert!
- Avoid opening suspicious links or downloading unsolicited attachments.
- Do not copy and paste code unless that is part of their job responsibilities
- Report ANY suspicious emails via Phish Alarm.