This content is viewable by Everyone
Aug 2025: Clickfix MacOS Attacks
Threat Alert: Clickfix MacOS Attacks
- Web-based threat actors known for distributing malware through compromised websites have been detected using ClickFix lures designed specifically for MacOS users.
- These threat actors tailor malware based on the location and device type of visitors to the compromised websites. In this case, the lures resulted in the delivery of Poseidon Stealer.n appear or are installed alongside benign applications, but may include adware, spyware, or other downloaders.
How is it used in the wild?
- Potential victims receive a seemingly normal marketing email or newsletter from a trusted contact. The message contains links that lead to a legitimate but compromised website.
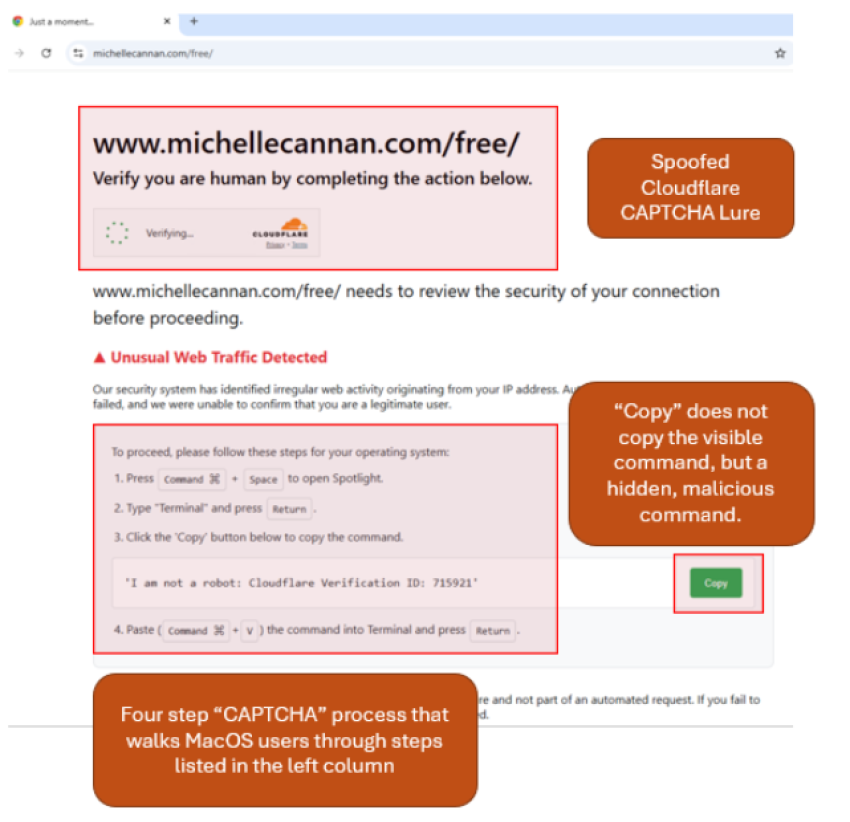
- The website checks the visitor’s location, language, and OS to determine if they are a suitable target for malware. If the user passes these checks and is on a MacOS device, a new version of a ClickFix lure designed for Apple users is displayed, instructing them to:
- Select Command + Space to open Spotlight
- Type “Terminal” and select Return
- Copy a command provided by the webpage
- Select Command + V to paste it, then select Return
- Copying and executing the malicious command results in the installation of Poseidon Stealer on the MacOS device.
Key Action: Stay Alert!
- Be aware of behaviors that indicate a site is compromised, including prompting browser updates, unfamiliar CAPTCHA processes, and anything using keyboard shortcuts.
- Never install software from an unknown source.
- Avoid interacting with links or attachments in unsolicited email.
- Report ANY suspicious emails via Phish Alarm.