This content is viewable by Everyone
Jul 2025: TA584 IMPERSONATES ADP - EMAIL LURE ATTACK
Threat Alert: TA584 IMPERSONATES ADP - EMAIL LURE ATTACK
- TA584 is a financially motivated large-crime threat actor known for employing well-crafted lures coupled with spoofed websites using fake CAPTCHAs in malware attacks.
- The threat actor is attempting to socially engineer victims into installing XWorm, a remote access trojan (RAT), by spoofing the popular enterprise payroll firm ADP.
How is it used in the wild?
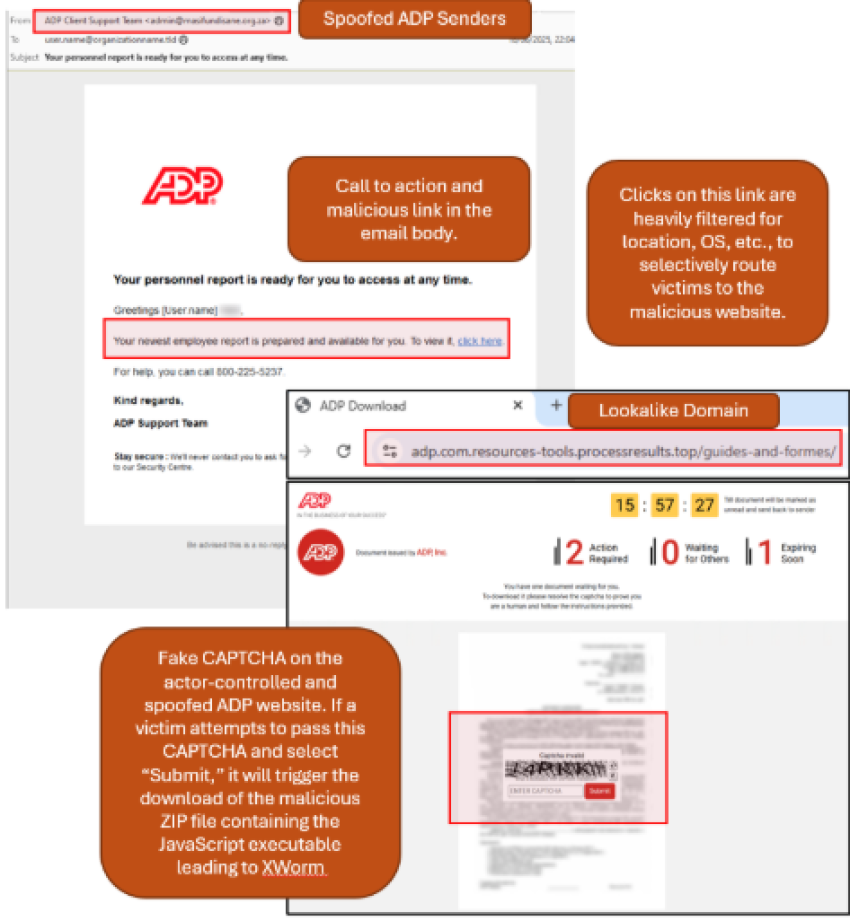
- TA584 sends emails purporting to originate from ADP. These messages state the recipient has a ”personnel report ready to access.”
- Messages appear to be from the “ADP Client Support Team.” However, a closer look reveals they are sent from various fraudulent or compromised senders.
- Links in the message body redirect through a traffic redirection system to an actor-created website spoofed to look like ADP.
- The malicious website is well-designed, complete with a dynamic clock counting down and a fake CAPTCHA challenge to download “one document waiting for you.”
- If the victim solves the CAPTCHA, a zipped JavaScript file containing XWorm will download. XWorm is installed if the victim extracts and executes the JavaScript file.
Key Action: Stay Alert!
- Be suspicious of unsolicited messages from external senders: interrogate headers and browser address bars for spoofed senders and lookalike domains.
- Use a trusted bookmark to log into accounts instead of following links in unsolicited emails.
- Report ANY suspicious emails via Phish Alarm.