This content is viewable by Everyone
May 2023: Phishing Attacks Impersonate Secure Share Providers
Threat Alert: What to Watch For
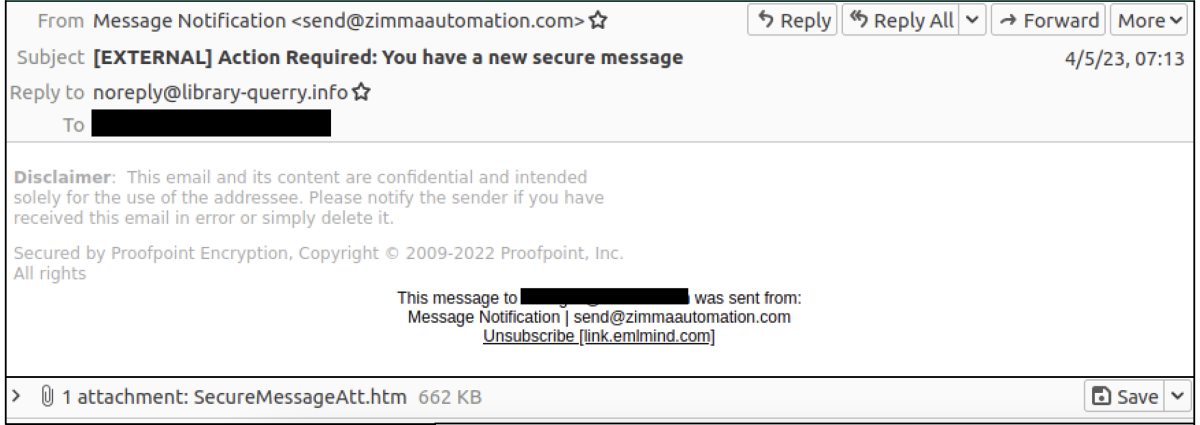
- Attackers have launched a series of phishing attacks impersonating reputable secure share providers, which are used for securely sharing files.
- The lures contain links or attachments containing the supposed document.
- Interacting with the link or attachment leads to the installation of credential harvesting malicious software (malware).
- The sending address for the emails does not match the expected company domain for the secure share provider.
Key Action: Report Suspicious Emails
- Report ANY suspicious emails using the Phish Alarm button in your email menu bar.
- Remember: Our organization occasionally sends phishing simulations that are used to evaluate the potential impact of a real phishing attack. Report any emails that match the tactics described above.
- If a reported message is a simulation, you will see a notification alerting you to that. No further action is needed on your part.
- If a reported message was not a simulation, and you are concerned about a time-sensitive request, you must take additional steps to verify the email is valid before acting on it.
Tips to Remember (at Work and at Home)
- Go beyond surface clues. Familiar logos, branding, and names are not automatic indicators that an email or website is safe. Cybercriminals often imitate well-known organizations.
- Verify the legitimacy of any unsolicited/unexpected email before you interact with it, especially if it directs you to click on a link. It can be tempting to click on a “call-to-action.” But if you notice a subtle change or inconsistency within a message claiming to be from HR or another internal department, don’t ignore it—report it.
- Independently navigate to company-leveraged secure share portals. Whenever possible, navigate to secure share sites directly as opposed to following a link or attachment in an email.