This content is viewable by Everyone
News
Know Your Role in Protecting UCSF Data
-
Author: Esther Silver
- Date:
- Associated Services:
Institutional information – data – is increasingly becoming UCSF’s lifeblood and most critical asset. Concurrently, data is growing enormously in complexity and volume while regulatory requirements are becoming ever more stringent. With the onset of Artificial Intelligence and Large Language Models, this trend stands to increase. These factors have made the data management process progressively more important.
Everyone at UCSF has a role to play in protecting our data. UCSF 650-16 Addendum A - UCSF Roles and Responsibilities for Securing Institutional Information and IT Resources describes these roles and their key responsibilities. Everyone, at a minimum, is a “workforce member” and must adhere to UC Policy BFB-IS-3: Electronic Information Security and UCSF Policy 650-16: Information Security and Confidentiality. People and Units have additional responsibilities based on their role within the institution. For example, a unit that manages data like employee information, financial data, or medical records is an “Institutional Information Proprietor” and must assign the related responsibilities to individuals within the unit. Another example is a department that delivers a particular IT service, as they would then own the responsibilities of a “Service Provider.” Additional information to help you understand your responsibilities is available in the UCOP Quick Start Guide by Role.
Valuable guidance on how to use and manage your data is available on the UCSF Data Resources webpage.
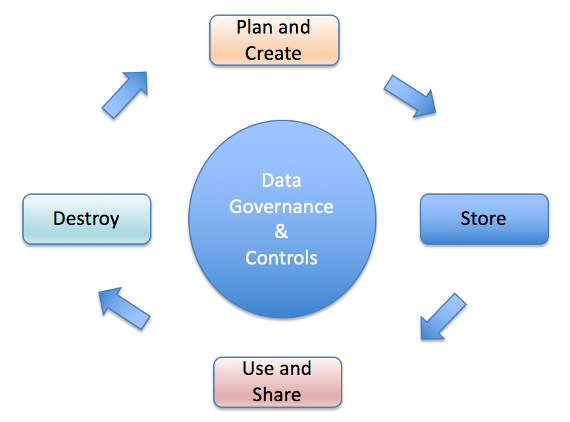
Data Security Lifecycle
Proper oversight of data throughout its life cycle is critical to optimize its utility and minimize the potential for errors and breaches. Below are examples of questions that should be asked, and measures taken within each of the four phases pictured above.
Plan
- What is the data classification? UCSF Policy 650-16 Addendum F, UCSF Data Classification Standard describes how to properly classify, work with, and secure your data based on UC policies that require impacts to be measured in the following areas:
- Loss of critical UCSF operations
- Negative financial impact (actual money lost, lost opportunities, value of the data itself)
- Damage to UCSF’s reputation
- Potential for regulatory or legal action
- Violation of UCSF’s mission, policies, or principles
- Requirement for corrective action or repairs
- What regulatory requirements apply to the data? Regulations that protect the security and privacy of data are on the rise. UCSF is subject to many of these regulations, including the following:
- Is a risk assessment required? UCSF is required by a number of laws, regulations, and policies to assess the risk of compromise to information systems that create, store, process, or transmit UCSF data, and any new system that will handle P3 (sensitive) or P4 (restricted) data must undergo a security risk assessment. The UCSF risk assessment process collects information about the security controls implemented on a system or application and uses that information to score its security compliance.
- Based on the data classification, what are the policy, legal, and access requirements? UCSF Policy 650-16 Addendum F, UCSF Data Classification Standard describes the policy, legal, and access requirements for each type of data.
- How will the data be kept safe? UCSF Policy 650-16 Addendum B, UCSF Minimum Security Standards for Electronic Information Resources describes the minimum-security measures for UCSF data and should be used to create a data management plan that addresses:
- System Inventory and Protection Level Classification (PLC)
- Transmission of Restricted Information
- Physical Security
- System Management Agent
- Network Access Control (NAC)
- Anti-Virus
- Host-Based Firewall
- Security Endpoint Detection and Response Agent (EDR)
- Device Encryption
- Authentication
- Passwords
- Software Patch Updates
- Application and Website Security
- Enterprise Vulnerability Management
Store
- How will the data be stored? Measures should be taken to ensure continued compliance with UCSF Policy 650-16 Addendum B, UCSF Minimum Security Standards for Electronic Information Resources.
- How do we know what data storage platforms are offered to UCSF staff, faculty, and learners and how to use them? UCSF IT provides information on Data Storage Options and Best Practices.
- How is the data backed up? UCSF IT provides Backup Services for servers as well CrashPlan for the data that reside on your desktop or laptop.
- How do we ensure the platform where the data is stored continues operations in the event of disaster or other interruption? As part of the risk assessment process, a business impact analysis is required to determine the impact of the platform being down and the minimum continuity measures.
Use and Share, Including Transmitting Data Electronically
- How will the data be used and shared? Measures should be taken to ensure continued compliance with UCSF Policy 650-16 Addendum B, UCSF Minimum Security Standards for Electronic Information Resources. In addition, UCSF has a task force dedicated to this question as it relates to third parties and has a list of recommendations. The UCSF Research Development Office has additional guidelines and templates.
- How will data be emailed? Secure email may be used by starting the subject with any of the following keywords (note that they must be the exact spelling and spacing to work properly):
- PHI:
- ePHI:
- Secure:
- [encrypt]
- Has consent been granted to share the data? If the research involves human subjects, obtain the proper informed consent documents.
- If you’ll be using or sharing de-identified health information, how is the data de-identified? Options for obtaining validated de-identified data sets include: requesting de-identified data as part of the UCSF Enterprise Data Request Process (must go through MyAccess – link to form is on the page); utilizing data from UCSF de-identified data applications; or requesting validation of your own de-identified data set. UCSF IT recommends ArcherHall LLC for de-identification certification but there are others.
- How is information (data) published and copyrighted? The UCSF library provides guidance on copyright, publishing, and intellectual property.
Destroy
- How long should the data be kept? Data should be stored in accordance with the UC Records Retention Schedule.
- How is paper media destroyed? Secure disposal bins should be used. Your manager can order one from the vendor, Shred-it, by contacting their customer service at 1-800-MYSHRED (1-800-697-4733) or [email protected] and creating a requisition in BearBuy.
- How is electronic media destroyed? Contact the IT Service Desk or call 415-514-4100. IT will collect and arrange for the destruction of any electronic media (hard drives, tapes, etc.) that contains restricted or sensitive data, including PII (personally identifiable information) and PHI (patient health information), free of charge.
- Can data be left in the cloud or in the possession of a third party after a project is completed? If your data is stored in a cloud-hosted environment or with a vendor, be sure to work with them to retrieve or properly dispose of your data. UCSF purchasing agreements have specific requirements for how vendors must handle disposition of UCSF data at the end of the agreement.
Take the quiz on protecting your data. Everyone who passes the quiz is entered to win one of six $50 Amazon Gift Cards.
Additional Information
- Chancellor’s Campus Messages: ChatGPT/Open AI Usage at UCSF
- UCSF’s Data Resources
- Owning Team: IT Security
-
Team Lead: Patrick Phelan