This content is viewable by Everyone
Oct 2025: Cl0p EXTORTION LURES
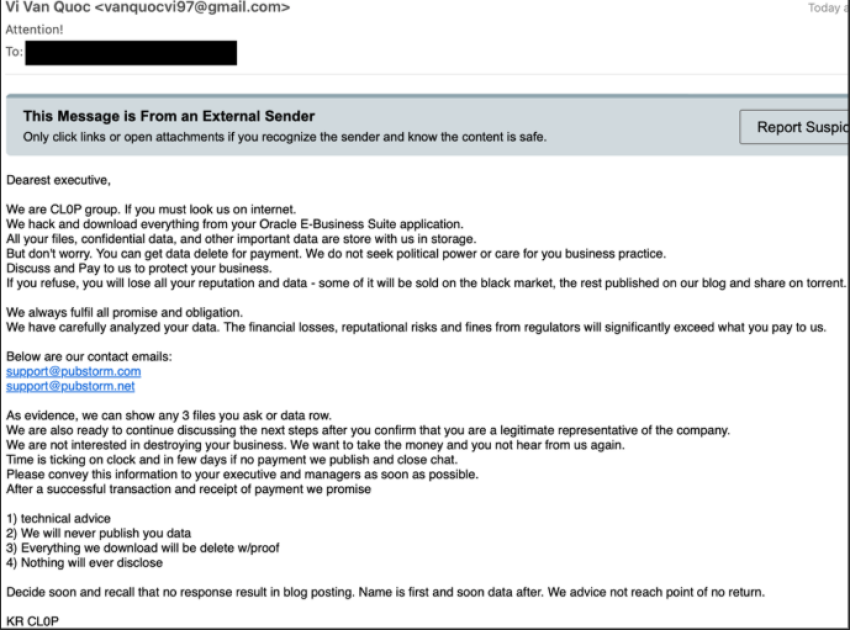
Threat Alert: Cl0p EXTORTION LURES
- Threat actors claiming to be from Cl0p or associated groups reach out to purported victims, claiming that sensitive or personal data has been stolen. Cl0p is a sophisticated crime group that engages in software supply chain vulnerability exploitation, ransomware deployment, and data theft to extort victims.
- These messages are meant to pressure victims into paying a ransom to prevent disclosure of data and have been assessed as legitimate threats. However, various scam extortion emails are common and are typically fake claims meant to extract funds from the target.
How is it used in the wild?
- The threats emerged from various senders and used a variety of subject lines, likely destined for executives or high-level staff.
- The messages claim that the group has exploited vulnerabilities in Oracle E-Business Suite and exfiltrated sensitive data.
- Threats instruct the recipient organizations to contact the group via included emails. These emails are listed on Cl0p’s data leak site.
- There are no reports of ransomware deployment at this time; instead, activity is focused on data theft and extortion. Oracle has released a patch for a newly discovered vulnerability, and some victims have since confirmed data exfiltration by Cl0p.
Key Action: Stay Alert!
- Stay Vigilant: Report any extortion attempts to the Service Desk immediately:
- Phone: 415-514-4100
- Email: [email protected]
- Web: http://help.ucsf.edu
- Don’t Rush: Carefully evaluate and investigate claims of data exfiltration before responding to extortion messages.
- Report ANY suspicious emails via Phish Alarm.