This content is viewable by Everyone
Oct 2025: DEVICE CODE PHISHING
Threat Alert: DEVICE CODE PHISHING
- A threat actor distributed multiple lures as
part of an infection chain designed to trick users into granting them access to victim accounts and devices. These attacks spoofed Microsoft authentication. - This is a high-volume threat actor that typically spoofs Microsoft OneDrive, LinkedIn, and DocuSign, but does not have a clear or consistent pattern of targeting. It has used compensation-related lures in the past.
How is it used in the wild?
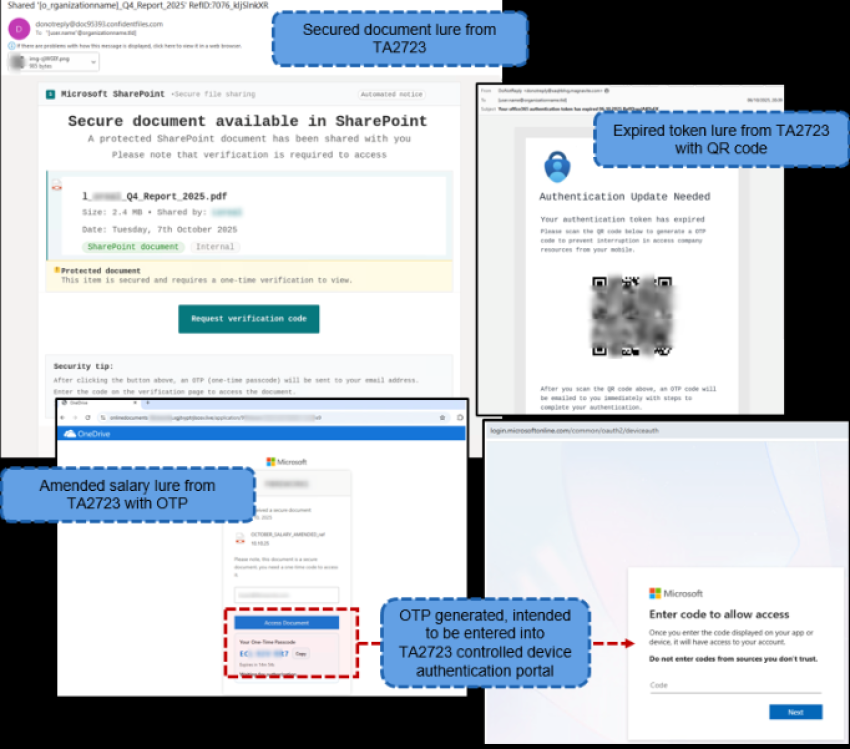
- The threat actor distributed email with various lures in early October, either impersonating an amended salary notification for some recipients, or masquerading as a generic secured document.
- The former messages contained a link prompting a user to generate a one-time password (OTP) in a secondary email; then, users were redirected to a legitimate device authentication page from Microsoft.
- The latter messages contained a QR code that generated an OTP in a secondary email, along with a link to a device authentication portal.
- In both cases, users are then provided an actor-controlled portal to input device authentication information. If provided, the threat actor gained access to victim accounts and endpoints.
Key Action: Stay Alert!
- Do not engage with spoofed emails by looking closely at headers and senders of suspicious or unsolicited emails.
- Don't provide your credentials to to unknown portals or landing pages.
- Do not scan QR codes in unsolicited emails or otherwise unknown sources.
- Report ANY suspicious emails via Phish Alarm.