Log in to see all content. Some content is hidden to the public.
Can't find what you're looking for? Help us improve the search functionality by reporting the expected results.
160 Results
Aug 2023: Phishing Attacks Abuse Proofpoint Branding
Threat Alert: Phishing Attacks Abuse Proofpoint Branding
Feb 2024: 2024 Tax-Themed Lures
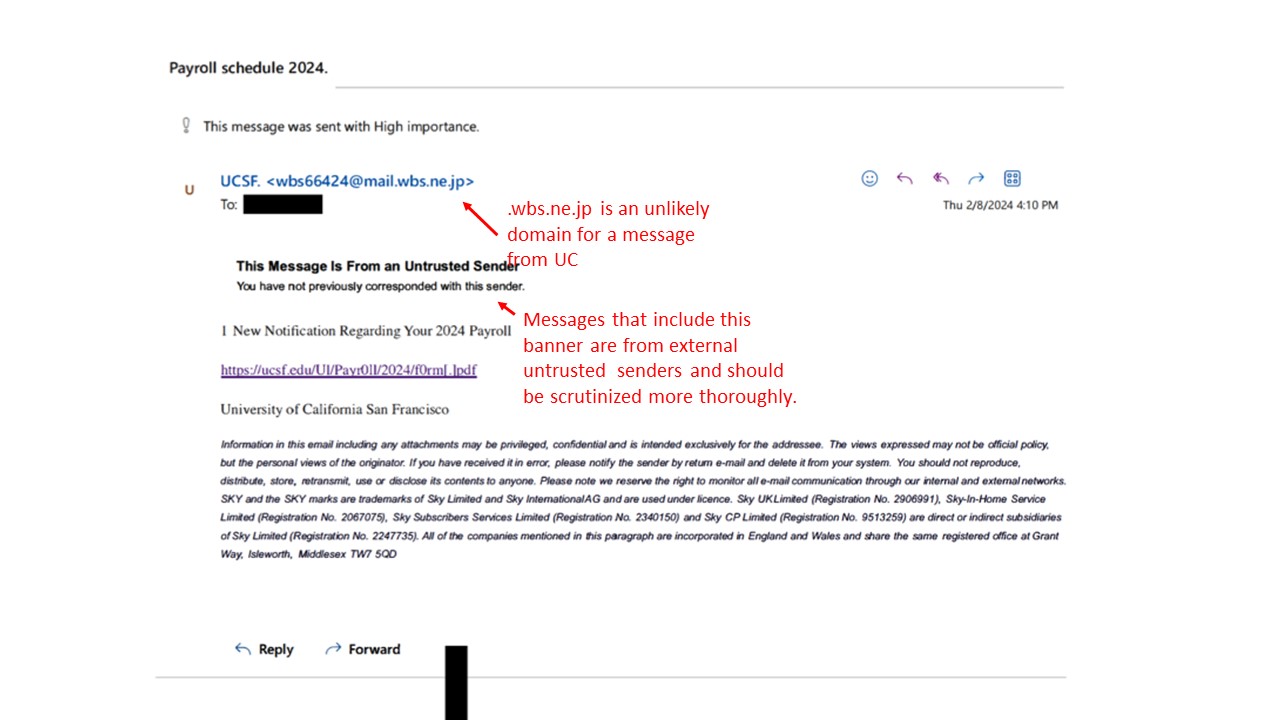
Feb: 2024: Real Phish Received at UCSF - Payroll Lure Harvesting Credentials
Picture of Actual Phish:
Picture of Actual Landi
Jan 2024: NHS-Themed Lures Steal Microsoft Credentials
Cybercriminals have launched a series of phishing attacks using spoofed or compromised email accounts belonging to the National Health Service (NHS). These emails, which appear to come from a NHS[.]net email address, use the subject line “YOU NEED TO SETTLE THIS.” A fully capitalized subject line like this is unlikely to come from an official government institution. The lures contain a prompt to review an alleged DocuSign document.
Feb 2024: Job Offer Message Lures
Threat Alert: Job Offer Message Lures
Email Tagging
- Affiliate
- Faculty
- Staff
- Student
- Technical Partner
- Volunteer
Digital Armor: Essential Security Tools for Protecting Your Devices
The link to the quiz is at the end of the art
Using Add-ins in Outlook Web App
Add-ins in Outlook.com are programs or utilities that help you automate tasks when you view or create messages.NOTE: You will need to install add-ins within Outlook to be able to use them in your work at UCSF.The following steps will assist you with locating and installing add-ins within Microsoft Outlook.1. Select the Apps icon (Outlook Web App (OWA)
- Affiliate
- Faculty
- Researcher
- Staff
- Student
- Email & Collaboration
Dec 2022: Microsoft OneDrive and QR Codes Used in Phishing Campaign
Recent email-based attacks have used compromised Microsoft OneDrive accounts to send phishing emails. These emails encourage recipients to click a link to view a shared document. The OneDrive links lead targets to shared PDF documents containing quick response (QR) codes.
Aug 2023: Geek Squad-Themed Lures Used in TOAD Attacks
Recent phishing emails are masquerading as notifications alerting the recipient to an automatic renewal of Best Buy’s Geek Squad Total Protect & Webroot Advance Threat Protection. The emails, however, do not use Best Buy sending addresses. Unlike many traditional phishing attacks, the emails do not include malicious links or attachments.