Log in to see all content. Some content is hidden to the public.
Can't find what you're looking for? Help us improve the search functionality by reporting the expected results.
3163 Results
High and Other Vulnerabilities in Pixel Devices
Google released a security update to address Critical and other vulnerabilities in Pixel Devices.For a complete description of the vulnerabilities and affected systems go to: Pixel Update Bulletin—February 2024.IT SecurityRead more about IT Security service offerings.
Vulnerabilities in Chrome
Google has released new versions of Chrome.For a complete description of the vulnerabilities and affected systems go to: Chrome Releases.IT SecurityRead more about IT Security service offerings.
Critical and Other Vulnerabilities in Android Devices
Google released its February Android update to address Critical and other vulnerabilities in Android Devices.For a complete description of the vulnerabilities and affected systems go to: Android Security Bulletin—February 2024.IT SecurityRead more about IT Security service offerings.
Critical Vulnerabilities Affecting Docker-Related Components
Moby and Open Container Initiative Released Critical Updates for Multiple Vulnerabilities Affecting Docker-related Components. A cyber threat actor could exploit these vulnerabilities to take control of an affected system.For a complete description of the vulnerabilities and affected systems go to:
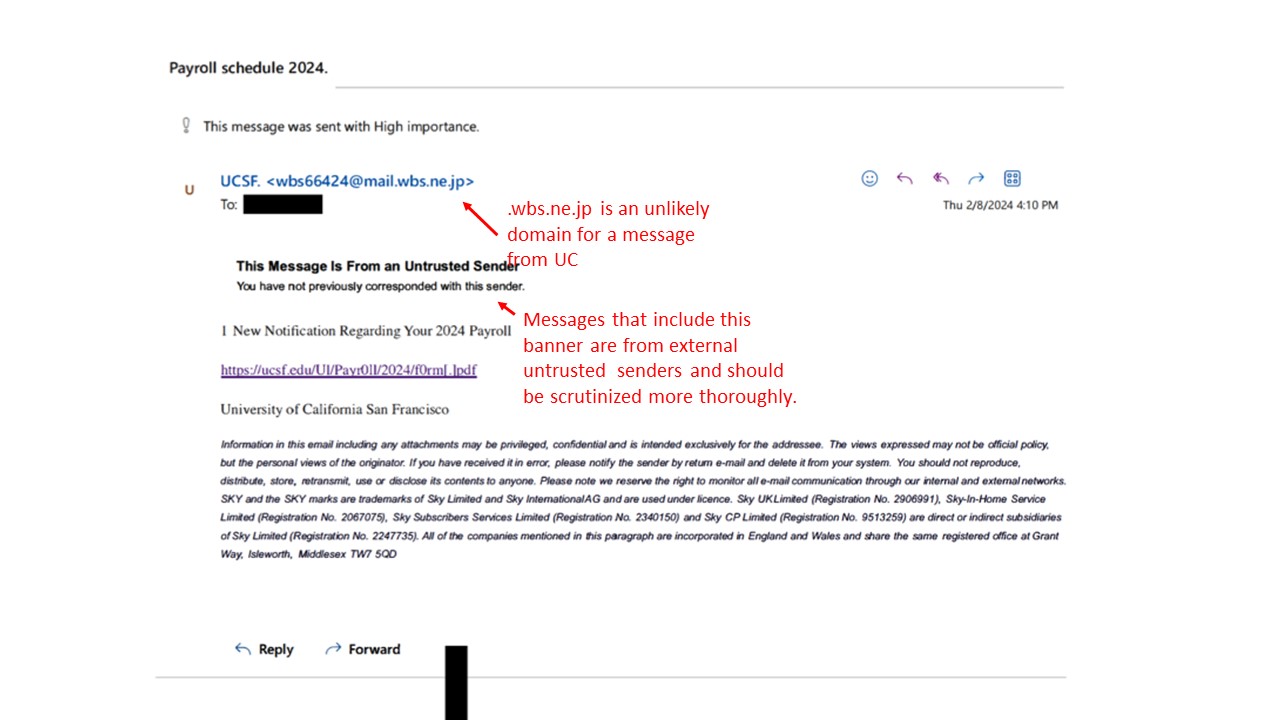
Feb: 2024: Real Phish Received at UCSF - Payroll Lure Harvesting Credentials
Picture of Actual Phish:
Picture of Actual Landi
Feb 2024: Deepfake Scam Imitating CFO
Threat Alert: Deepfake Scam Targeting Financial Transactions An employee attended a video conference call with seemingly authentic colleagues, all of whom were later revealed to be deepfake representations. The worker, initially suspicious of a phishing email, was convinced by the realistic appearance and voices of the deepfake participants during the video call. Subsequently, the employee authorized a large financial transaction, thinking it was a legitimate request initiated by the CFO.
Office of the CIO
In support of UCSF’s most important priorities, the Office of the CIO teams facilitate the alignment of IT people, strategy, investments, and the IT operating model.
Jan 2024: Policy Update Phishing Lures Bypass MFA
Threat Alert: Company Policy Phishing Lures Bypass MFA
Vulnerabilities in Various Red Hat Products in January 2024
Red Hat released multiple security updates in January for various Red Hat products. For a complete description of the vulnerabilities and affected systems go to: Red Hat Security Advisories.IT SecurityRead more about IT Security service offerings.
Vulnerabilities in Various Suse Products in January 2024
Suse released multiple security updates in January for various Suse products.For a complete description of the vulnerabilities and affected systems go to: Suse January 2024 Archives by date.IT Security