This content is viewable by Everyone
Dec 2025: AI TRADING BOT LURE
Threat Alert: AI TRADING BOT LURE
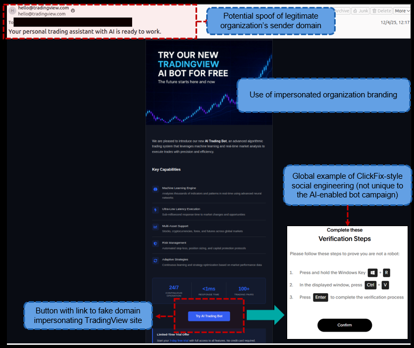
- Threat actors impersonated TradingView, a legitimate platform used for charting and analysis focused on stock trading and investments, using an AI-enabled trading assistant lure.
- Threat actors seek to capitalize on themes related to AI-enabled technologies and tooling to deceive users in email-based message lures and wider social engineering frameworks.
How is it used in the wild?
- Message lures claimed to be announcements that TradingView introduced a new AI Trading Bot that leveraged advanced AI-enabled capabilities to enhance market analysis and execute precision trades.
- The messages contained a button labeled “Try AI Trading Bot”, which was a link to the lookalike domain ai-tradingview[.]com. If opened, the URL led to a website that impersonated TradingView
- Upon visiting the site, users encountered a ClickFix social engineering prompt designed to convince them to execute a malicious script on behalf of the threat actor that led to the installation of malware (DcRAT and zgRAT).
Key Action: Stay Alert!
- Be aware of potential lookalike web pages. Always look for signs of potential web page impersonation. Be sure to check the URL carefully. Some impostor sites use URLs that very closely resemble the legitimate URL.
- Use approved software and tools. If you need to download or update a specific utility or application, follow UCSF's specified processes or reach out to the Service Desk for help.
- Remain alert to phishing indicators. Mismatches between sending addresses and an organization’s name are always warning signs. AI-enabled tools enhance the quality of lures, so stay alert for less obvious signs of malicious intent, including messages tailored to specific regions and languages.
- Report ANY suspicious emails via Phish Alarm.