This content is viewable by Everyone
Dec 2025: BONUS-RELATED DOCUSIGN LURES
Threat Alert: BONUS-RELATED DOCUSIGN LURES
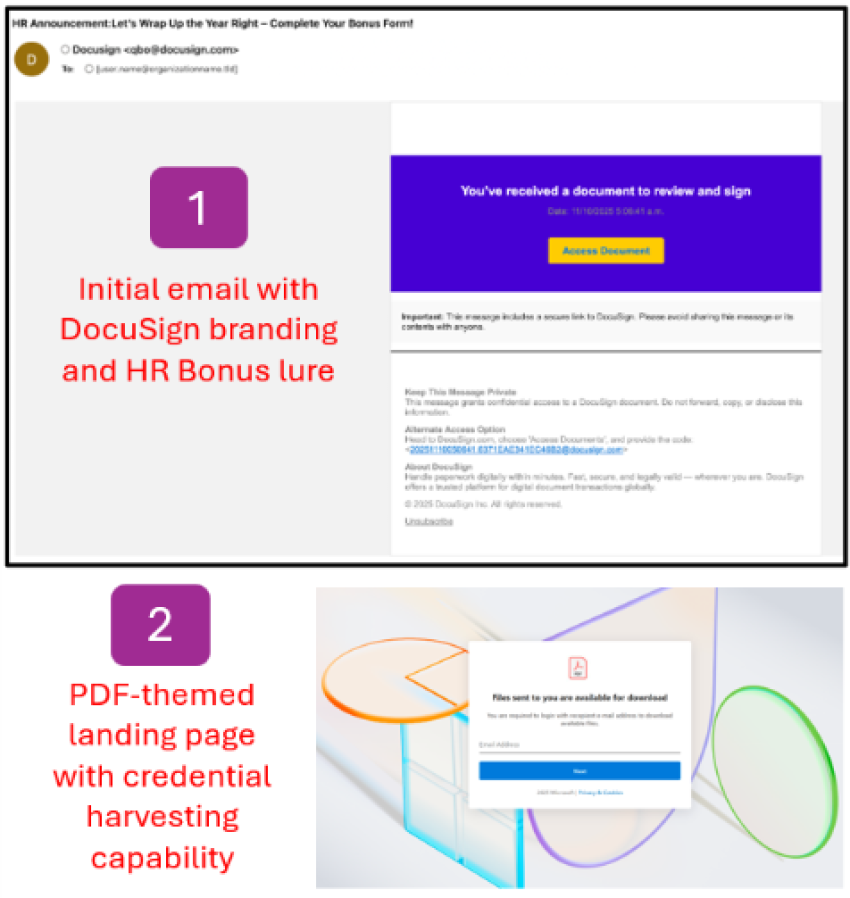
- Threat actors impersonate DocuSign in a credential phishing campaign with the intention of collecting user credentials and payment information.
- The campaign used HR bonus-related lures to create urgency and trick users into opening malicious links.
- This tactic has been used multiple times in the past, commonly occurring toward the end of the year—coinciding with legitimate HR documentation.
- End users are directed through a chain of redirects, ultimately leading to a PDF-themed credential harvesting page.
How is it used in the wild?
- Messages are sent appearing to be from DocuSign (qbo@docusign[.]com) with the subject “HR Announcement: Let’s Wrap Up the Year Right – Complete Your Bonus Form.”
- The initial link is from docsend[.]com, a legitimate document sharing platform owned by DropBox that was abused by the threat actor. After redirecting through multiple landing pages, the end user is directed to a PDF-themed credential harvesting page.
- Threat actors collect both user credentials and payment information through this campaign.
Key Action: Stay Alert!
- Be extremely cautious of any urgent HR or bonus-related messages, especially those requiring immediate action.
- Know where legitimate UCSF HR-related communications will come from, so you have a baseline to compare potentially anomalous traffic to.
- Make a practice of scrutinizing message headers for spoofed senders. And be wary of messages that elicit an emotional response, such as notifications around pay.
- Remain alert to phishing indicators. Mismatches between sending addresses and an organization’s name are always warning signs.
- Report ANY suspicious emails via Phish Alarm.