Overview
Guide to Dependabot for GitHub Enterprise: What works, what's in the works. Covers Alerts, Security Updates, and Version Updates.
Quick Setup (Start Here)
👩💻 Developers
- What even is Dependabot?
- The Three Pillars of Dependabot
- Customizing Dependabot PR Workflows
- Tip: Check your Notification Settings
- Video Tutorial
- References
Org Admin Tasks (Do Once per Org)
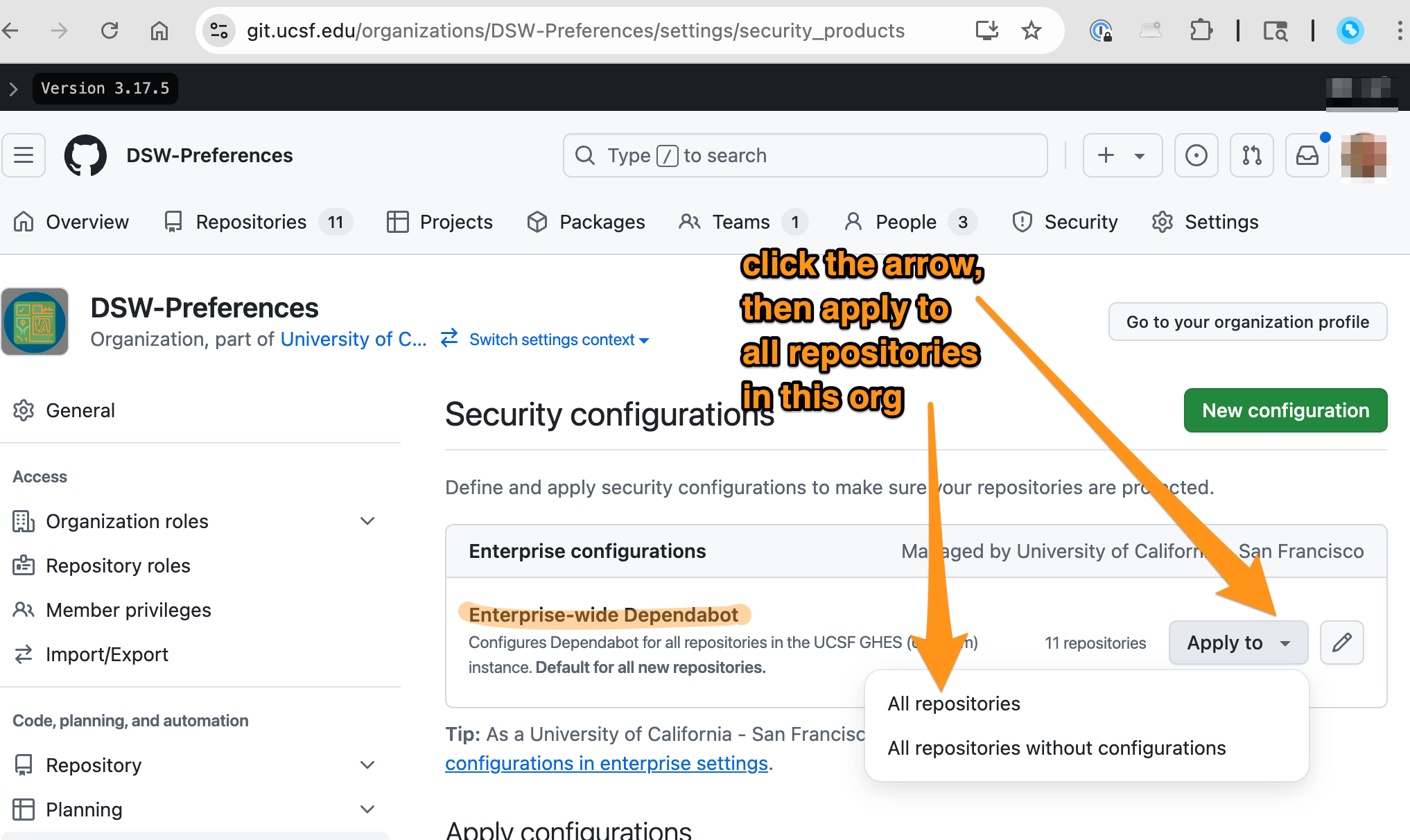
1. Enable enterprise-wide features
Go to Org Settings → Advanced Security → Configurations
Apply Enterprise-wide Dependabot to all repositories
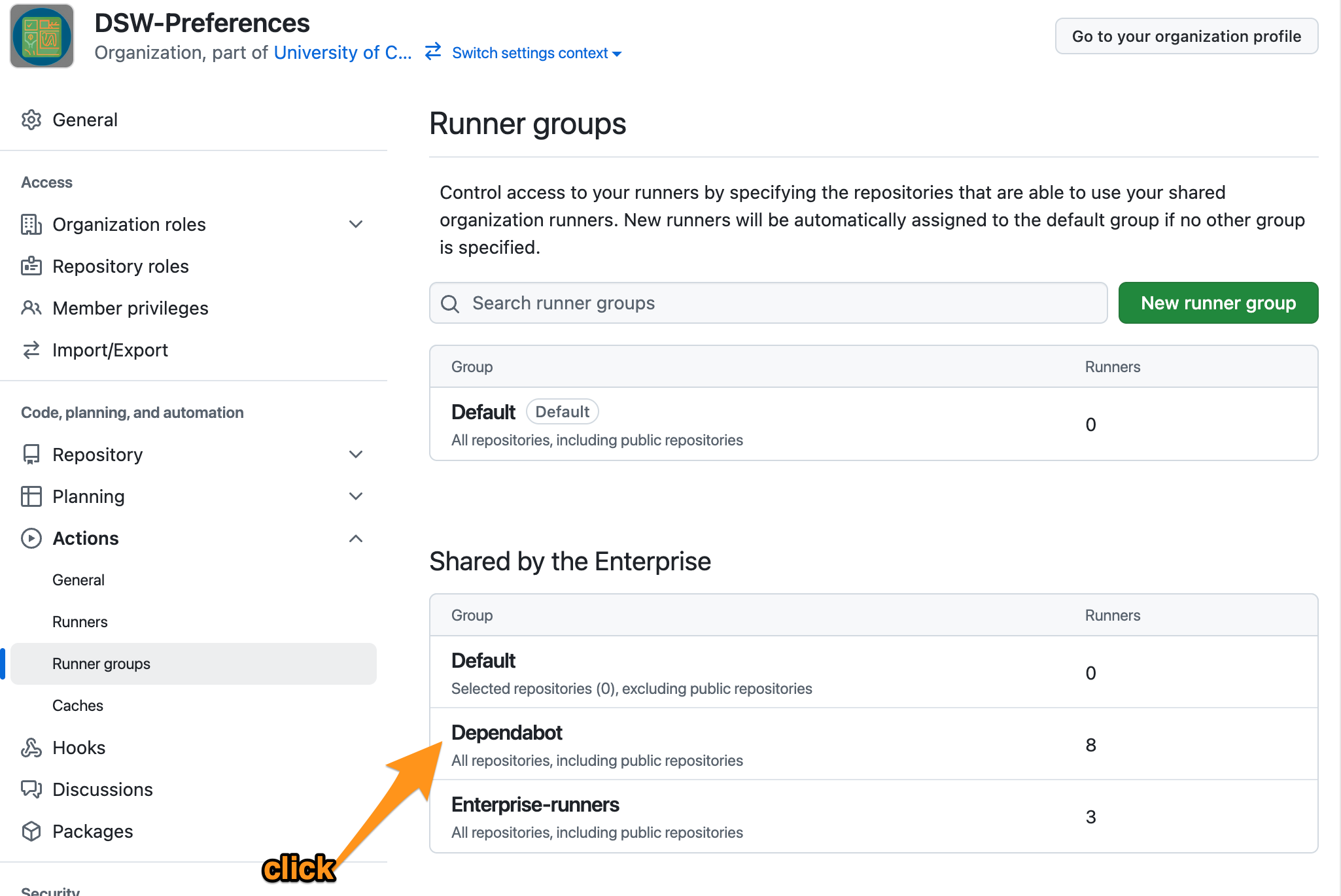
2. Configure Dependabot runner access
Org Settings → Actions → Runner groups
Select Dependabot runner group
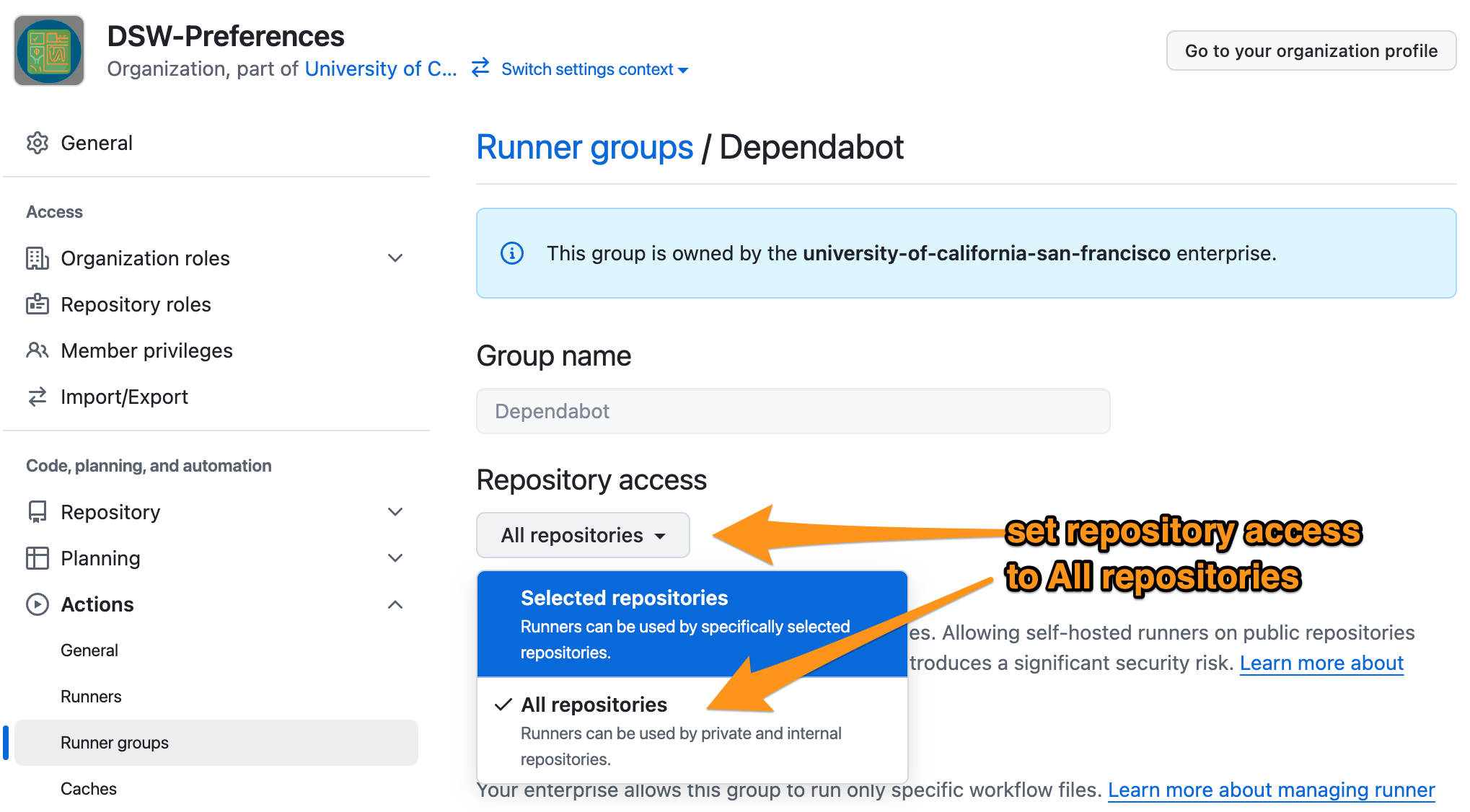
Set repository access = All repos (recommended)
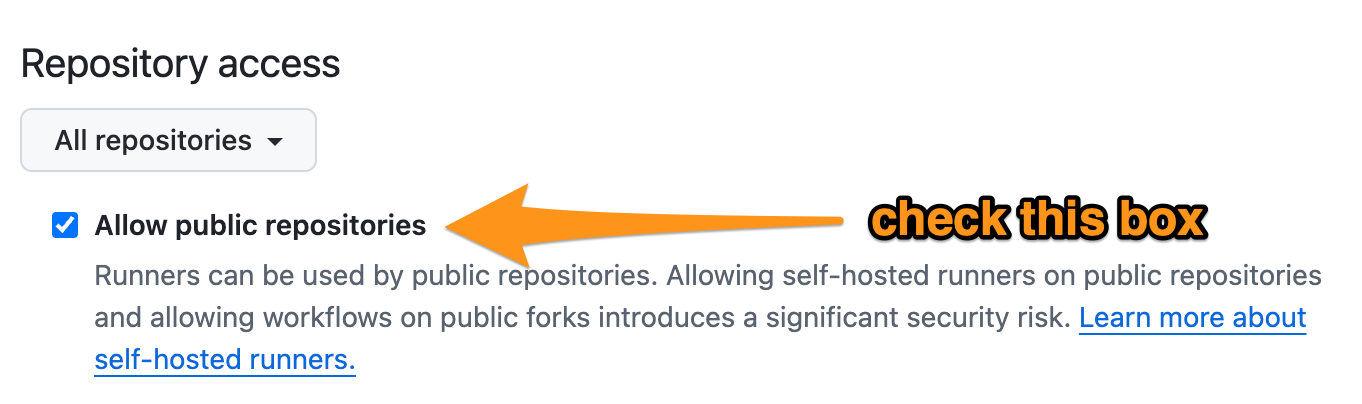
If you have “public” repos (GHES = UCSF-wide, still firewall-protected), check Allow public repositories
Repo Admin Tasks (Per Repository)
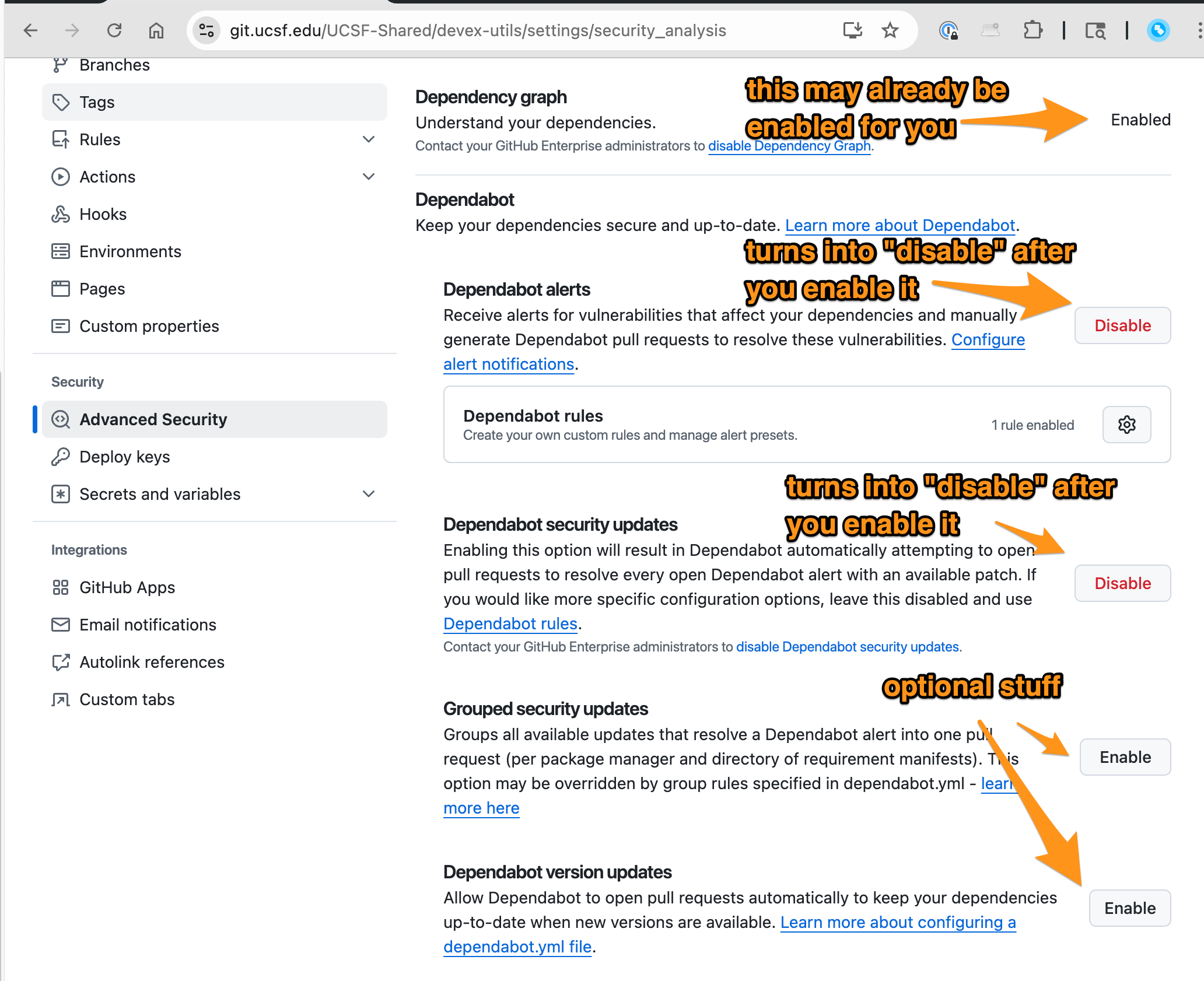
1. Turn on security features
Repo Settings → Advanced Security
Enable Dependency graph (probably already enabled for you)
Enable Dependabot alerts
Enable Dependabot security updates
✅ Done when both toggles show “Disable” in red (yes, it's confusing)
Optionally enable Dependabot Version Updates (up to you, but it's a nice service)
Optionally enable Grouped Security Updates (if you'd rather just merge a batch of security updates all at once... we have no recommendation here, some people like this feature, some people hate it)
2. Add configuration file
Create
.github/dependabot.ymlDefine package ecosystems, update intervals, reviewers
✅ Done when PRs appear on schedule
Example: .github/dependabot.yml
Developers (Day-to-day use)
1. Review Dependabot PRs
Treat Dependabot PRs like normal contributor PRs
Ha ha, you're so funny. No, seriously, you should be reviewing all PRs you receive in a timely manner
Just so you know, if you ignore Dependabot PRs long enough, it will stop sending them to you, until you interact with one of them in some way
Merge the PR if tests pass and changes look safe
2. Customize CI/CD for Dependabot PRs
If you'd like to automate how your repository reacts to Dependabot PRs (completely optional, and kind of a flex, honestly), add .github/workflows/dependabot.yml (more details on this below, see Customizing Dependabot PR Workflows):
name: Dependabot PR Workflow
on: pull_request
jobs:
dependabot:
runs-on: devex-arc-runner-set
if: ${{ github.actor == 'dependabot[bot]' }}
steps:
- name: Skip intensive tests
if: contains(github.event.pull_request.title, 'bump')
run: echo "Skipping intensive tests"
- name: Auto-label PR
uses: actions/github-script@v6
with:
script: |
github.rest.issues.addLabels({
issue_number: context.issue.number,
owner: context.repo.owner,
repo: context.repo.repo,
labels: ['dependencies']
})
What even is Dependabot?
Dependabot consists of several distinct (though similarly-named) features in GitHub Enterprise Server (GHES), each requiring specific configuration and infrastructure. This guide is specific to the on-premise GitHub Enterprise server, and covers:
- Dependabot Alerts: Notification system for known vulnerabilities
- Dependabot Security Updates: Automated pull requests to fix vulnerabilities via configuration file
- Dependabot Version Updates: Scheduled dependency updates via configuration file
ℹ️ Note: The following features are already configured at the enterprise level:
- Dependency graph enabled
- Dependabot alerts enabled
- Required GitHub Actions runner deployed
What about GHEC (GitHub Enterpise Cloud)? Here are some articles on Dependabot for GHEC:
- https://github.blog/changelog/2024-04-22-dependabot-updates-on-actions-for-github-enterprise-cloud-and-free-pro-and-teams-users/
- https://docs.github.com/en/code-security/getting-started/dependabot-quickstart-guide
The Three Pillars of Dependabot
Think of Dependabot as three parts:
Feature | Purpose | Needs Config File? | Who Sets It Up? | Output |
|---|---|---|---|---|
Alerts (⚠️ Warn) | Warn about known vulnerabilities | No | Repo Admin | Security alerts in GitHub |
Security Updates (🔒 Fix) | Auto-PRs to patch vulnerabilities | Yes ( | Repo Admin + Org Admin | PRs with security fixes |
Version Updates (♻️ Maintain) | Scheduled dependency bumps | Yes ( | Repo Admin | PRs with version updates |
Customizing Dependabot PR Workflows
You can control how your repository responds to Dependabot PRs by creating a custom workflow. This allows you to:
- Skip certain CI/CD jobs for Dependabot PRs
- Add specific labels or reviewers automatically
- Customize PR handling based on dependency type
Create or modify .github/workflows/dependabot.yml:
name: Dependabot PR Workflow
on: pull_request
jobs:
dependabot:
runs-on: ubuntu-latest
if: ${{ github.actor == 'dependabot[bot]' }}
steps:
# Example: Skip certain tests for dependency updates
- name: Skip intensive tests
if: contains(github.event.pull_request.title, 'bump')
run: echo "Skipping intensive tests for dependency update"
# Example: Auto-label Dependabot PRs
- name: Label PR
uses: actions/github-script@v6
with:
script: |
github.rest.issues.addLabels({
issue_number: context.issue.number,
owner: context.repo.owner,
repo: context.repo.repo,
labels: ['dependencies']
})
ℹ️ Note: This workflow only triggers on Dependabot PRs thanks to the condition if: ${{ github.actor == 'dependabot[bot]' }}
Tip: check your notification settings
🔔 Note: To get the most out of Dependabot, check your notification settings for security alerts:
- Go to your GitHub profile settings
- Navigate to "Notifications" → "System"
- Choose how you want to receive Dependabot alerts: New vulnerabilities
- On GitHub
- CLI
- Choose how often you want to receive the Email weekly digest
- Don't send
- Send weekly
- Send daily
While you're reviewing your notification settings, you might want to review all of them. If you've found GitHub to be a bit too noisy about changes, you can tweak your settings here.
Video Tutorial
[1] “About Dependabot Alerts (GHES)” https://docs.github.com/en/enterprise-server@latest/code-security/dependabot/dependabot-alerts/about-dependabot-alerts
[2] “Enabling Dependabot for Private Repositories (GHES)” https://docs.github.com/en/enterprise-server@latest/code-security/dependabot/dependabot-alerts/configuring-dependabot-alerts
[3] “Configuring Security Updates (GHES)” https://docs.github.com/en/enterprise-server@latest/code-security/dependabot/dependabot-security-updates/configuring-dependabot-security-updates
[4] “Version Update Configuration Options (GHES)” https://docs.github.com/en/enterprise-server@latest/code-security/dependabot/dependabot-version-updates/configuration-options-for-the-dependabot.yml-file
[5] “GitHub Advisory Database” https://github.com/advisories
[6] "Automating Dependabot with GitHub Actions" https://docs.github.com/en/code-security/dependabot/working-with-dependabot/automating-dependabot-with-github-actions
[7] "Configuration options for the dependabot.yml file" https://docs.github.com/en/code-security/dependabot/dependabot-version-updates/configuration-options-for-the-dependabot.yml-file