Log in to see all content. Some content is hidden to the public.
Can't find what you're looking for? Help us improve the search functionality by reporting the expected results.
652 Results
Nov 2022: Twitter-Themed Lures Used in Credential Phishing Attacks
Cybercriminals have launched phishing attacks impersonating Twitter Services. The emails include links to lookalike landing pages that are designed to steal Twitter credentials and phone numbers. While the email display names make it appear the messages come from “Twitter Services,” the actual sending address is a Gmail account. The emails use the proposed change at Twitter of charging verified users a monthly fee to maintain their verification status.
Oct 2023: TOAD Attack Spoofs Best Buy’s Geek Squad Branding
Threat Alert: TOAD Attack Spoofs Geek Squad Branding
Dec 2023: Eventbrite-Themed Lures Distribute Malware
Threat Alert: Eventbrite-Themed Lures Distribute Malware
May 2023: AI-Themed Phishing Lures Distribute Threats
Cybercriminals have launched a campaign distributing malware with an AI-themed lure. The lure purports to be from an “Information Technology Manager” regarding a mandatory system update for employees. The email body directs recipients as to how they can download the new AI-powered software.
Research Electronic Data Capture (REDCap) Programming
REDCap software enables investigators to develop online survey instruments and databases. Our team runs an instance of REDCap in our data center that is distinct from the REDCap environment offered by Academic Research Systems (ARS).
- Affiliate
- Research Staff
- Researcher
- Staff
- Student
- Research Services
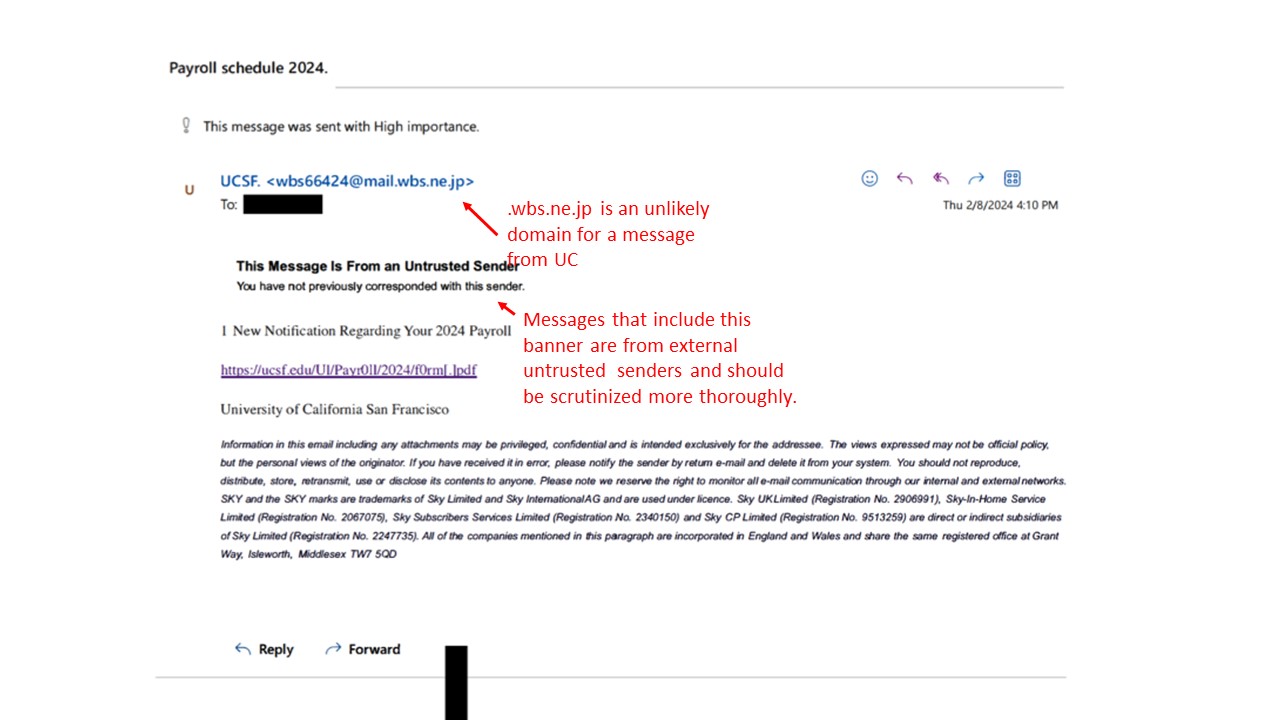
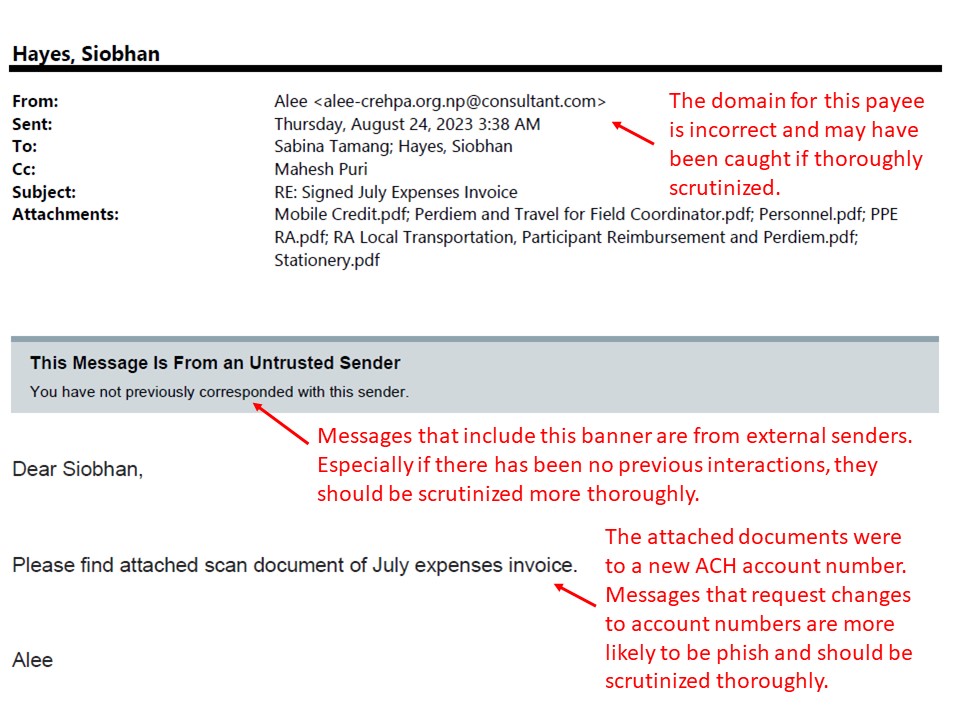
Feb: 2024: Real Phish Received at UCSF - Payroll Lure Harvesting Credentials
Picture of Actual Phish:
Picture of Actual Landi
Mar 2023: Attacks Spread Microsoft Teams-Themed Lures
Cybercriminals have launched phishing attacks using lures that impersonate Microsoft Teams meeting invites. The lures include a malicious link. Clicking the malicious link leads to a credential phishing kit that redirects the user to a legitimate login page.
May 2023: Phishing Attacks Impersonate Secure Share Providers
Attackers have launched a series of phishing attacks impersonating reputable secure share providers, which are used for securely sharing files. The lures contain links or attachments containing the supposed document. Interacting with the link or attachment leads to the installation of credential harvesting malicious software (malwa