Duo provides users with the following authentication methods:
- Duo Push: Default verification method for Duo users with a smart device, and UCSF IT’s recommended method for multi-factor authentication. This requires a smartphone or tablet (running Android or iOS) with the Duo Mobile application installed and enrolled to your Active Directory account, and an internet connection.
- Duo Passcode: Alternate option for verification; this also requires the Duo Mobile application installed to a smart device but does not require an internet connection.
- YubiKey: Physical USB key that you plug into a computer to provide secondary authentication. NOTE: YubiKeys are not available to UCSF Health Saint Francis and UCSF Health St. Mary's hospital employees. While, YubiKeys will not be offered in the future to UCSF employees, existing YubiKeys will be supported and it is recommended to request a token if you are not able to use your smartphone or tablet with Duo.
- Token: A hard token generate passcodes used for multi-factor authentication.
Duo Push
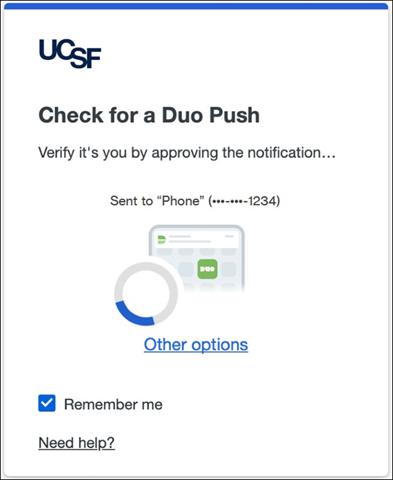
1. Enter your UCSF email address and password in a Duo-enabled application (e.g., MyAccess, Outlook Web Access).
2. Duo will automatically send you a push notification to your Duo enrolled device.
NOTE: Duo will send a Duo Push as a default. If you are accessing MyAccess or an application directly from MyAccess such as UCPath, you will be asked to complete a Duo Verified Push. Learn more about Duo Verified Push.
3. A Duo push notification will appear on your device.
4. Tap the notification to open the Duo Mobile app.
5. On the prompt, select the Approve button to complete your login.
NOTE: Be sure to review the information on the Duo Push to ensure that the information is correct and that you initiated the push notification.
6. Select whether to remember the device you are using by selecting Yes, this is my device for any device that only you use and trust. By remembering your device, you will not be required to provide authenticate with Duo for 16 hours. NOTE: If you are using a public or shared device, select the No, other people use this device option.
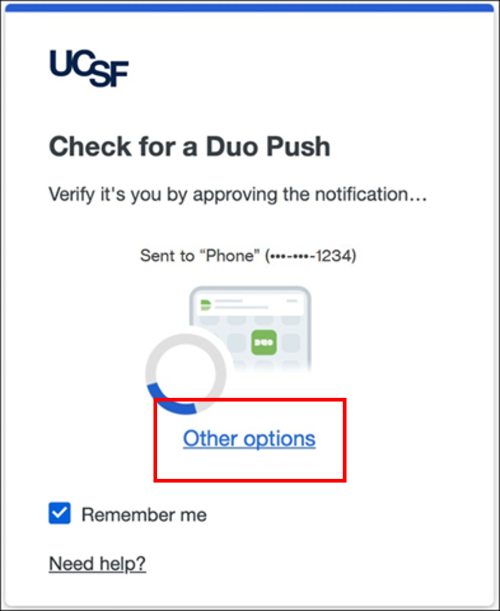
Other Options
Select If you are unable to prefer not to use the recommended Duo Push verification, you may select one of the other available verification methods detailed below.
NOTE: Duo will always default to a Push, so you will have to follow this process each time you wish to use an alternate verification method.
Duo Mobile Passcode
1. When you receive the screen to Check for a Duo Push, select Other Options.
2. Select Duo Mobile passcode.
3. Launch the Duo Mobile app on your device and expand the UCSF entry. A six-digit passcode will appear. NOTE: You will have to refresh the passcode after every use; this code is only valid for one-time use.
4. Enter the six-digit passcode on the device you are attempting to log into, then select Verify.
5. Select whether to remember the device you are using by selecting Yes, this is my device for any device that only you use and trust. NOTE: If you are using a public or shared device, select the No, other people use this device option.
YubiKey
A YubiKey is a physical security device that plugs into your computer's USB port to provide two-factor authentication. Since a YubiKey grants access to your UCSF computing accounts, be sure to keep it in a safe place at all times, and do not leave your YubiKey plugged into or near your computer unattended. Report a lost or stolen YubiKey immediately. Replacement YubiKeys cost $30 each.
NOTE: While YubiKeys will not be offered in the future to UCSF employees, existing YubiKeys will be supported and it is recommended to request a token if you are not able to use your smartphone or tablet with Duo.
Requesting a YubiKey
- Go to http://help.ucsf.edu and select Accounts, Access & Email.
- Log into MyAccess with your network login username and password.
- Select Duo YubiKey (Two-Factor USB Device) Request Form.
- Fill out the form and click Submit. Your YubiKey should be delivered to UCSF IT within two business days.
- You will receive a notification to pick up your YubiKey from an IT Health Desk location.
- Locate the closest IT Health Desk and bring your photo ID so we can verify your identity.
Using a YubiKey
1. Insert the YubiKey into your computer’s USB port.
2. On the Check for a Duo Push, select Other Options.
3. Select YubiKey passcode.
4. Select the Passcode field and press your YubiKey button to enter before selecting the Verify button.
5. Select whether to remember the device you are using by selecting Yes, this is my device for any device that only you use and trust. NOTE: If you are using a public or shared device, select the No, other people use this device option.
Token
1. Enter your UCSF email address and password in a Duo-enabled application such as MyAccess, VPN, or Outlook Web App
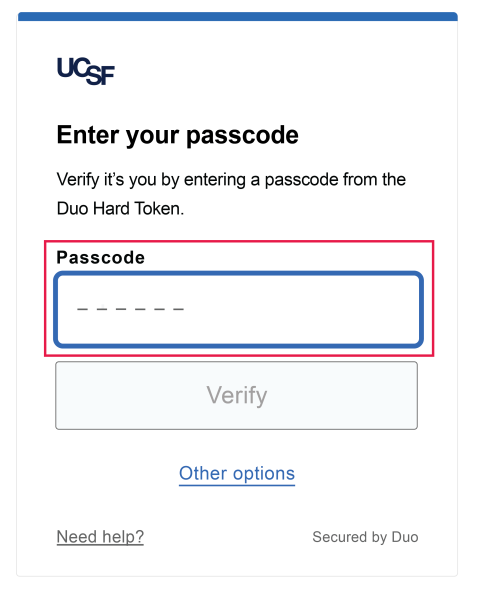
2. When the Duo Screen loads, select the Other Options link
3. From the Other Options to log in screen, select the Hard Token Option
4. Press the Green button on your token to generate a one-time use six-digit passcode
5. Enter the six-digit passcode from your Duo Token into Duo before selecting the Verify button to be logged into the desired system or application