Log in to see all content. Some content is hidden to the public.
Can't find what you're looking for? Help us improve the search functionality by reporting the expected results.
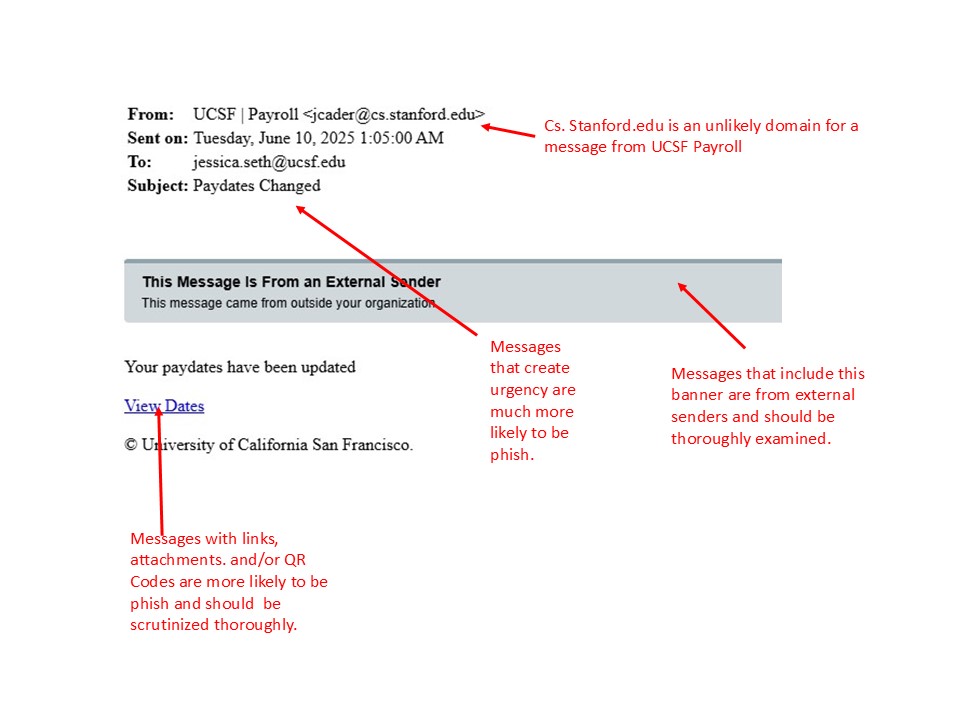
155 Results
- Other Content
Zero Day Attack on Zimbra Enterprise Email Solution
Zimbra released security updates to address a vulnerability in Zimbra Enterprise Email Solution that is being actively exploited. An unauthenticated attacker could exploit this vulnerability to steal cleartext credentials from a targeted Zimbra instance without any user interaction. For a complete description of the vulnerabilities and affected systems Zimbra Product Releases. IT Security
Oct 2023: Business Email Compromise Lures Spoof US Fire Administration
Threat Alert: BEC Lures Imitate US Fire Administration
Oct 2023: Dual-Purpose Phishing Attacks Use Blocked Email Lure
Threat Alert: Dual-Purpose Phish Use Blocked Email Lure
Aug 2023: USDA-Themed Lures Use Embedded URLs, QR Codes to Harvest Email Credentials
Threat Alert: USDA-Themed Lures Harvest Email Credentials
Jun 2025: Job Lure Phish!
Jun 2025: TxTag, You're It!
May 2025: Click Here to Unsubscribe