This content is viewable by Everyone
News
Don’t Let the Data Hit the Fan: Your Role in Protecting UCSF Data
-
Author: Esther Silver
- Date:
- Associated Services:
Learn about your role in protecting UCSF data and pass the quiz at the end of the article. You could win one of five $50 Amazon gift cards!
At UCSF, institutional information - data- has become the beating heart of our institution and is vital to everything we do. As the volume and complexity of data grow rapidly and regulatory demands tighten, effective data management has never been more crucial. Everyone at UCSF has a role to play in protecting our data. UCSF 650-16 Addendum A - UCSF Roles and Responsibilities for Securing Institutional Information and IT Resources describes these roles and key responsibilities.
All UCSF employees are considered “workforce members” and must adhere to UC Policy BFB-IS-3: Electronic Information Security, UCSF Policy 650-16: Information Security and Confidentiality, and, if UCSF Medical Center Systems are involved, Policy 5.01.06 Control of Access to and Release of Information from UCSF Medical Center Information Systems.
Additional information to help you understand your responsibilities is available in the UCOP Quick Start Guide by Role.
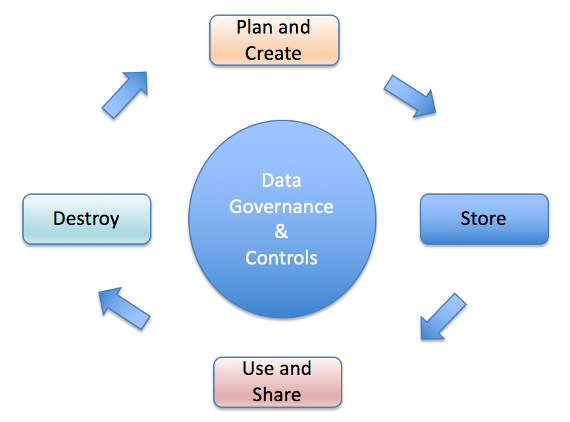
Data Security Lifecycle
Proper oversight of data throughout its life cycle is critical to optimize its utility and minimize potential errors and breaches. Below are examples of the measures that must be taken within each of the four phases pictured above.
Plan and Create
- Data Classification: "Data" refers to all Institutional Information in any format (e.g., electronic, paper-based, or fax). Properly classifying data will help determine the necessary safeguards needed to protect it, as well as ensure that these measures meet any necessary regulatory requirements. UCSF Policy 650-16 Addendum F, UCSF Data Classification Standard describes how to properly classify, work with, and secure your data based on UC policies that require impacts to be measured in the areas listed below
- Loss of critical UCSF operations
- Negative financial impact (actual money lost, lost opportunities, value of the data itself)
- Damage to UCSF’s reputation
- Potential for regulatory or legal action
- Violation of UCSF’s mission, policies, or principles
- Requirement for corrective action or repairs
Click here to watch the new, exciting three-minute video on Data Classification
- Adhere to Regulatory Requirements: Regulations that protect the security and privacy of data are on the rise. UCSF is subject to many of these regulations, including the following:
- Determine if a Risk Assessment is required: UCSF is required by several laws, regulations, and policies to assess, among other things, the risk of compromise to information systems that create, store, process, or transmit UCSF data. The UCSF risk assessment process collects information about the security controls and practices implemented on a system or application and uses that information to score its security compliance.
- Based on the data classification, determine what the policy, legal, and access requirements are: UCSF Policy 650-16 Addendum F, UCSF Data Classification Standard describes the policy, legal, and access requirements for each data type.
- Keep the data safe and secure: UCSF Policy 650-16 Addendum B, UCSF Minimum Security Standards for Electronic Information Resources describes the minimum-security safeguards for UCSF data and should be used to create a data management plan that addresses the following:
- System Inventory and Protection Level Classification (PLC)
- Transmission of Restricted Information
- Physical Security
- System Management Agent
- Network Access Control (NAC)
- Anti-Virus
- Host-Based Firewall
- Security Endpoint Detection and Response Agent (EDR)
- Device Encryption
- Authentication
- Passwords
- Software Patch Updates
- Application and Website Security
- Enterprise Vulnerability Management
Additionally, if Medical Center data is involved, Policy 5.01.06 Control of Access to and Release of Information from UCSF Medical Center Information Systems must also be followed.
Store
- Store the data safely and securely: Measures should be taken to ensure continued compliance with UCSF Policy 650-16 Addendum B, UCSF Minimum Security Standards for Electronic Information Resources, and Policy 5.01.06 Control of Access to and Release of Information if UCSF Medical Center Information Systems are involved. Data Storage Options and Best Practices provides insight into the various data storage options to help you select the best one that meets your specific requirements, as well as best practices for organizing and maintaining your data in accordance with UCSF policy.
- Backup the data: UCSF IT provides Backup Services for servers and OneDrive Sync for the data that resides on your desktop or laptop.
- Ensure the platform where the data is stored continues operations in the event of a disaster or other interruption: As part of the risk assessment process, a business impact analysis is required to determine the impact of the platform being down and the minimum continuity measures. Additionally, the page Disaster Recovery - Roles and Responsibilities describes the responsibilities for each applicable role in the disaster recovery process.
Use and Share, Including Transmitting Data Electronically
- Share data properly: Measures should be taken to ensure continued compliance with UCSF Policy 650-16 Addendum B, UCSF Minimum Security Standards for Electronic Information Resources, and Policy 5.01.06 Control of Access to and Release of Information from UCSF Medical Center Information Systems. In addition, UCSF has the Data Sharing Oversight Committee dedicated to the governance of shared data. They support the requirements for sharing UCSF data externally. More information is available at Requirements for Sharing Data Externally. The UCSF Research Development Office has additional grant guidelines and templates. The Policy 650-20: External Sharing of Personally Identifiable Information (PII) and PII-Derived Data must be adhered to when sharing Personally Identifiable Information (PII) and PII-Derived Data outside of UCSF. Lastly, all non-ARS analysts who extract data from APeX Clarity for research purposes are required to enroll in the Federated Research Data Steward (FReDS) Program.
- Email Securely: Secure email may be used by starting the subject with any of the following keywords (note that they must be the exact spelling and spacing to work correctly):
- PHI:
- ePHI:
- Secure:
- [encrypt]
- Obtain consent to share data: The Institutional Review Board’s approval is needed for human subjects research.
- If sharing de-identified health information, ensure it is adequately de-identified: The current sources of certified de-identified research health information at UCSF are the De-identified Clinical Data Warehouse and Information Commons. Obtaining data through the Clinical Data Research Consulting (CDRC) research data extraction service ensures that the resulting dataset will be correctly de-identified.
- Follow the minimum necessary standard: For example, at UCSF, we must limit the use and disclosure of patient information to the minimum necessary to complete the task. Doing so helps to protect patient privacy and reduces the risk of privacy incidents.
- Publish and copyright information properly: The UCSF library provides guidance on copyright, publishing, and intellectual property.
Destroy
- Retain the data for the correct amount of time: Data should be stored in accordance with the UC Records Retention Schedule.
- Destroy unneeded paper documents that might include protected information: Secure disposal bins should be used. Your manager can order one from approved vendors in BearBuy.
- Destroy electronic media that may contain protected information: Contact the IT Service Desk or call 415-514-4100. IT will collect and arrange for the destruction of any electronic media (hard drives, tapes, etc.) that contains restricted or sensitive data, including PII (personally identifiable information) and PHI (protected health information), free of charge.
- Ensure data maintained by third parties is appropriately managed at the end of projects: Per the Appendix Data Security (DS), at the end of a project, the supplier must return all Institutional Information to the University of California (UC) within thirty (30) calendar days of the termination, cancellation, expiration, or other conclusion of the Agreement. After returning the data, the supplier must dispose of the Institutional Information in its possession, as well as any data held by sub-suppliers or agents, using methods described in UC’s Institutional Information Disposal Standard or an alternative approved by UC
Take the quiz on protecting your data. Everyone who passes the quiz is entered to win one of six $50 Amazon Gift Cards.
Additional Information
- UCSF’s Data Resources
- Office of Healthcare Compliance and Privacy
- Forbes - Why The Data Security Lifecycle Is Essential For Reducing Cost And Risk
- Owning Team: IT Security
-
Team Lead: Patrick Phelan