Log in to see all content. Some content is hidden to the public.
Can't find what you're looking for? Help us improve the search functionality by reporting the expected results.
2523 Results
Zoom Patches Critical Vulnerability in Windows Applications
Zoom has released a security bulletin to address a critical vulnerability in its Windows applications. The attack is described as an improper input validation that could allow an attacker with network access to escalate privileges.For a complete description of the vulnerabilities and affected systems go to Zoom Security Bulletin.IT SecurityRead more about IT Security service offerings.
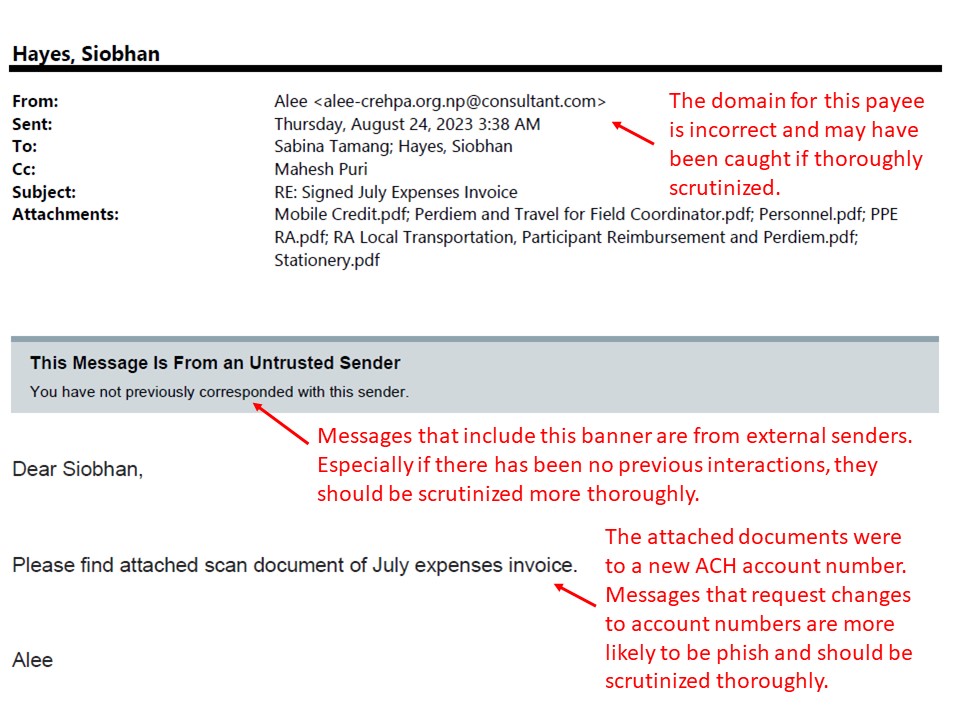
Jun - Nov 2023: Supply Chain Management / Accounts Payable ACH Fraud
Picture of One of the Phish
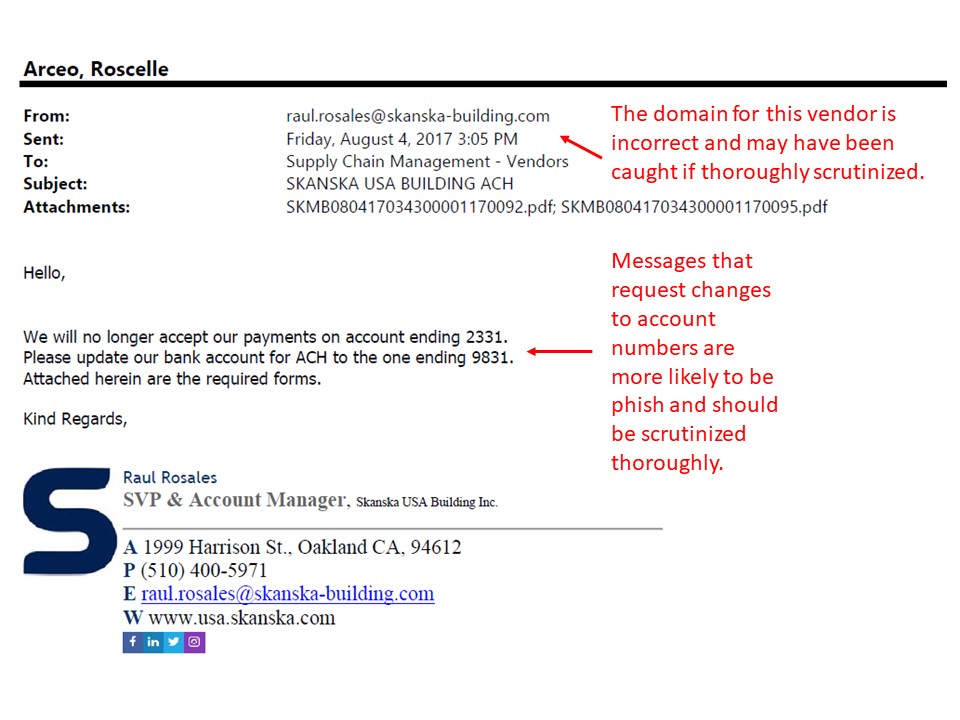
Aug 2017: Supply Chain Management / Vendor Relations ACH Fraud
Picture of Real Phish
Threat Alert: Fraudul
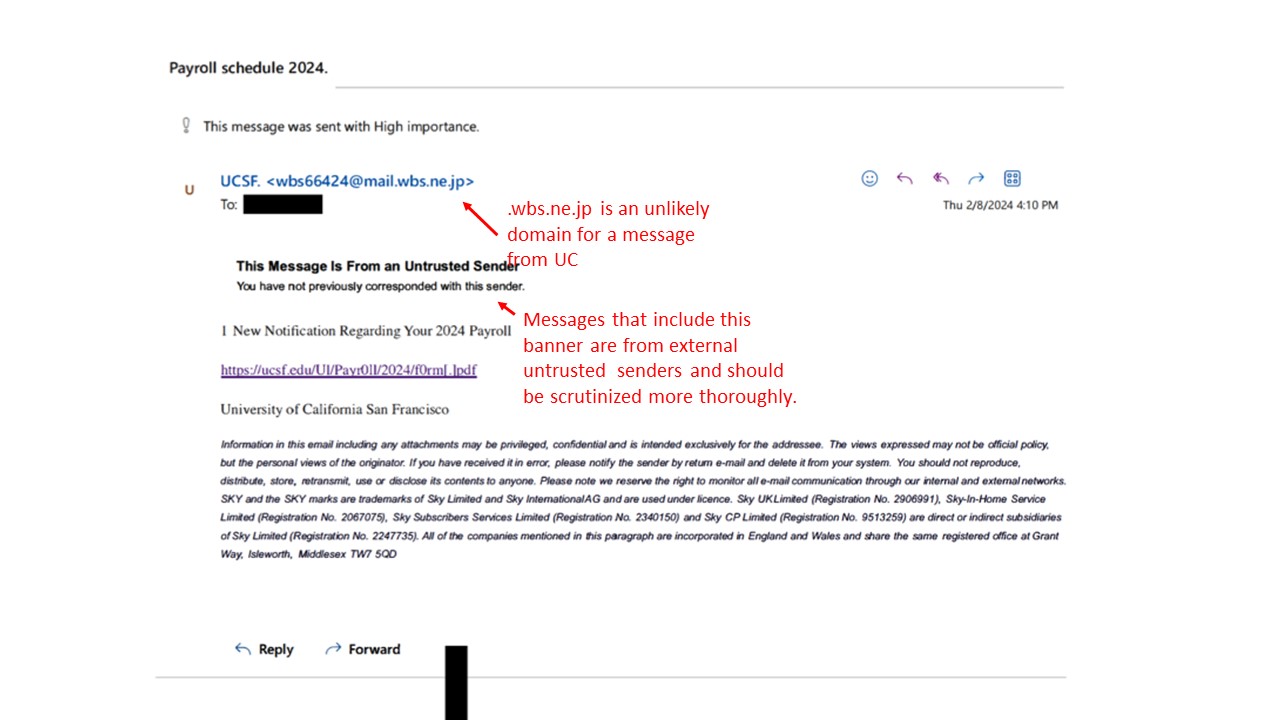
Feb: 2024: Real Phish Received at UCSF - Payroll Lure Harvesting Credentials
Picture of Actual Phish:
Picture of Actual Landi
Feb 2024: Deepfake Scam Imitating CFO
Threat Alert: Deepfake Scam Targeting Financial Transactions An employee attended a video conference call with seemingly authentic colleagues, all of whom were later revealed to be deepfake representations. The worker, initially suspicious of a phishing email, was convinced by the realistic appearance and voices of the deepfake participants during the video call. Subsequently, the employee authorized a large financial transaction, thinking it was a legitimate request initiated by the CFO.
Office of the CIO
In support of UCSF’s most important priorities, the Office of the CIO teams facilitate the alignment of IT people, strategy, investments, and the IT operating model.
Jan 2024: Policy Update Phishing Lures Bypass MFA
Threat Alert: Company Policy Phishing Lures Bypass MFA
Critical Vulnerability Impacting GoAnywhere MFT
The newly disclosed flaw is tracked as CVE-2024-0204 and is rated critical with a CVSS v3.1 score of 9.8 as it is remotely exploitable, allowing an unauthorized user to create admin users via the product’s administration portal. Creating arbitrary accounts with administrative privileges can lead to a complete device takeover. In the case of Go Anywhere MFT, that would allow attackers to access sensitive data, introduce malware, and potentially enable further attacks within the network.
Staffbase Add-In Missing in Account
As a communicator, I am attempting to send a communication to a large amount of users at UCSF through the Staffbase email add-in. When I attempt to access Staffbase from my resource account in the Outlook Web App, the Staffbase add-in does not appear when I select the add-ins icon. The following video and steps to follow will assist you in sending your communication despite the add-in being missing.
- Affiliate
- Faculty
- Staff
- Student
- Technical Partner
- Volunteer
- Email & Collaboration
Lantern Loader
Arjabi
About integration services team